How To Mitigate Emm Security Threats Techtarget
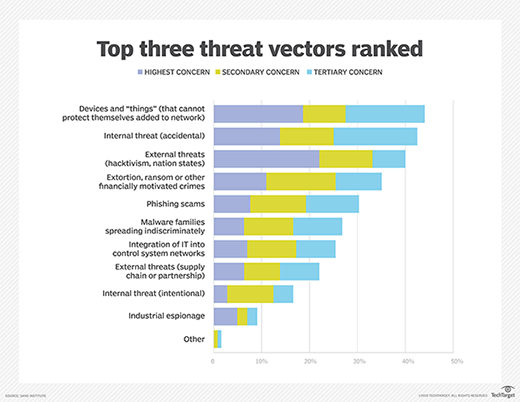
How To Mitigate Emm Security Threats Techtarget As malware advances, security can often be compromised on an emm platform. learn what steps it can take to ensure that their emm security is rock solid. Learn how to protect your mobile devices from emm security threats by following six steps that cover assessment, implementation, education, monitoring, updating, and staying informed of emm.

Cyber Security Management Strategies To Mitigate Threats Ppt Presentation Enterprise mobility management software allows it to deploy security policies and provide access to internal resources by integrating with apis in the mobile oses. It should use mobile threat defense to extend emm and to provide a critical component to secure mobile devices. the better the integration between the two platforms, the more effectively mobile threat defense can protect those devices. Symantec recently examined the very mobile incidents you want to mitigate at a real world fortune 500 company with more than 400,000 global employees. our team analyzed the threats that would've been successful if the company had relied on emm alone. As malware advances, security can often be compromised on an emm platform. learn what steps it can take to ensure that their emm security is rock solid.
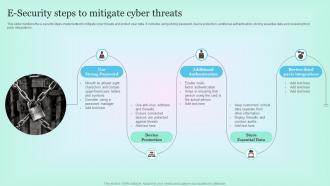
E Security Steps To Mitigate Cyber Threats Symantec recently examined the very mobile incidents you want to mitigate at a real world fortune 500 company with more than 400,000 global employees. our team analyzed the threats that would've been successful if the company had relied on emm alone. As malware advances, security can often be compromised on an emm platform. learn what steps it can take to ensure that their emm security is rock solid. To secure emm systems, it is essential to understand the threat landscape and the attack vectors that target mobile devices and emm components. common threats include malware and phishing,. By enforcing security policies, protecting data, and facilitating incident response, emm solutions play a vital role in safeguarding against emerging mobile threats, ensuring that organizations can harness the benefits of mobility without compromising on security. Understand the risks that come with mobile apps and how to mitigate them. the use of mobile devices within enterprise organizations is commonplace, so organizations must prepare for all sorts of mobile threat vectors including attacks via mobile applications to avoid a cybersecurity breach. This white paper will cover the security limits of emm alone and how important it is to have mtd protecting your organization from real world threats. specifically, we will look at some real world events when emm is not enough.
6 Ways To Mitigate External Security Threats Safety4sea To secure emm systems, it is essential to understand the threat landscape and the attack vectors that target mobile devices and emm components. common threats include malware and phishing,. By enforcing security policies, protecting data, and facilitating incident response, emm solutions play a vital role in safeguarding against emerging mobile threats, ensuring that organizations can harness the benefits of mobility without compromising on security. Understand the risks that come with mobile apps and how to mitigate them. the use of mobile devices within enterprise organizations is commonplace, so organizations must prepare for all sorts of mobile threat vectors including attacks via mobile applications to avoid a cybersecurity breach. This white paper will cover the security limits of emm alone and how important it is to have mtd protecting your organization from real world threats. specifically, we will look at some real world events when emm is not enough.
How Emm Solutions Safeguard Against Emerging Mobile Threats Understand the risks that come with mobile apps and how to mitigate them. the use of mobile devices within enterprise organizations is commonplace, so organizations must prepare for all sorts of mobile threat vectors including attacks via mobile applications to avoid a cybersecurity breach. This white paper will cover the security limits of emm alone and how important it is to have mtd protecting your organization from real world threats. specifically, we will look at some real world events when emm is not enough.
Implementing Strategies To Mitigate Cyber Security Threats Powerpoint
Comments are closed.