How To Encrypt Data In Transit And At Rest
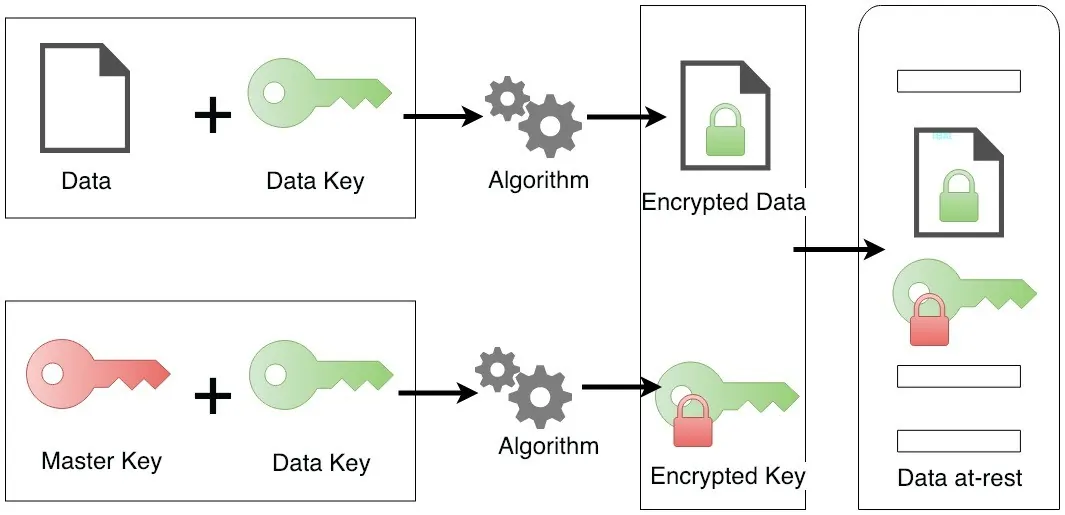
How To Encrypt Data At Rest And In Transit Its Using services like aws kms, aws cloudhsm, and aws acm, customers can implement a comprehensive data at rest and data in transit encryption strategy across their aws ecosystem to ensure all data of a given classification shares the same security posture. Each type requires specific encryption techniques for optimized protection, which we break down in detail below. if you want to learn more about data encryption, here’s a quick overview of this technology and how it works. watch this video to better understand at rest and in transit encryption.
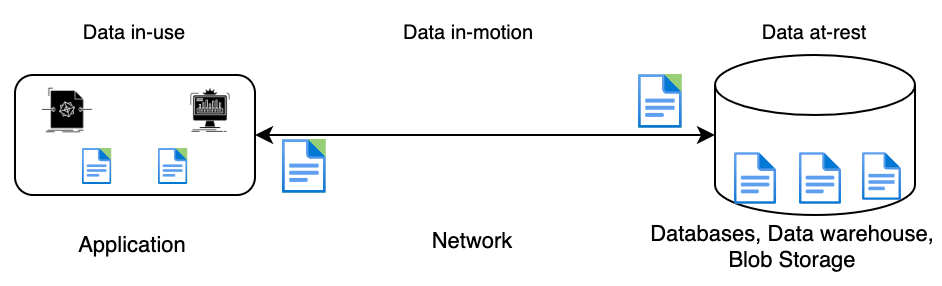
How To Encrypt Data At Rest And In Transit Its In this article, find a brief explanation of how microsoft encrypts microsoft 365 customer data in transit. We take a deep dive into data security. in particular, data at rest vs data in transit and how you can keep your organization's data protected. The first step in choosing the right encryption strategy is to understand the differences between three different states of data – in transit, at rest and in use – and the security challenges posed by each. In order to understand how to encrypt data in various states, we first need to look at the differences between the three states of data: at rest, in transit, or in use.

Encrypt Data At Rest And In Transit Using Strong Encryption Algorithms The first step in choosing the right encryption strategy is to understand the differences between three different states of data – in transit, at rest and in use – and the security challenges posed by each. In order to understand how to encrypt data in various states, we first need to look at the differences between the three states of data: at rest, in transit, or in use. Learn about approaches to data protection for data in transit vs. data at rest in data protection 101, our series on the fundamentals of data security. A short overview of the various data encryption methods available today: encryption in transit, encryption at rest and encryption end to end. Remember, encryption at rest ensures that your data takes a nap in a secure fortress whenever it's not in use, while encryption in transit guards your data as it journeys from one digital stop to another. Today, we're diving deep into the differences between encrypting data at rest and data in transit. by the end of this post, you'll understand the nuances of each, their importance, and how to implement them effectively.
Encryption Understanding Data At Rest Vs In Transit Datalocker Inc Learn about approaches to data protection for data in transit vs. data at rest in data protection 101, our series on the fundamentals of data security. A short overview of the various data encryption methods available today: encryption in transit, encryption at rest and encryption end to end. Remember, encryption at rest ensures that your data takes a nap in a secure fortress whenever it's not in use, while encryption in transit guards your data as it journeys from one digital stop to another. Today, we're diving deep into the differences between encrypting data at rest and data in transit. by the end of this post, you'll understand the nuances of each, their importance, and how to implement them effectively.
Comments are closed.