How Do Buffer Overflow Attacks Work

Buffer Overflow Attacks Pdf Buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain unauthorized access to corporate systems. discover what is a buffer overflow attack and how fortinet can mitigate and prevent overflow attacks. What is a buffer overflow attack and how does one work? exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables.

Buffer Overflow Attacks Pdf Computer Architecture Computer Data Many cyber attacks exploit buffer overflow vulnerabilities to compromise target applications or systems. here's is what you need to know, and what you can do to secure your applications. Attackers use buffer overflows to corrupt the execution stack of a web application. by sending carefully crafted input to a web application, an attacker can cause the web application to execute arbitrary code – effectively taking over the machine. How do attackers exploit buffer overflows? an attacker can deliberately feed a carefully crafted input into a program that will cause the program to try and store that input in a buffer that isn’t large enough, overwriting portions of memory connected to the buffer space. A computer program may be vulnerable to buffer overflow if it handles incoming data incorrectly. anybody who can provide suitably crafted user input data may cause such a program to crash or execute arbitrary code. learn how buffer overflow attacks work and how you can avoid them.
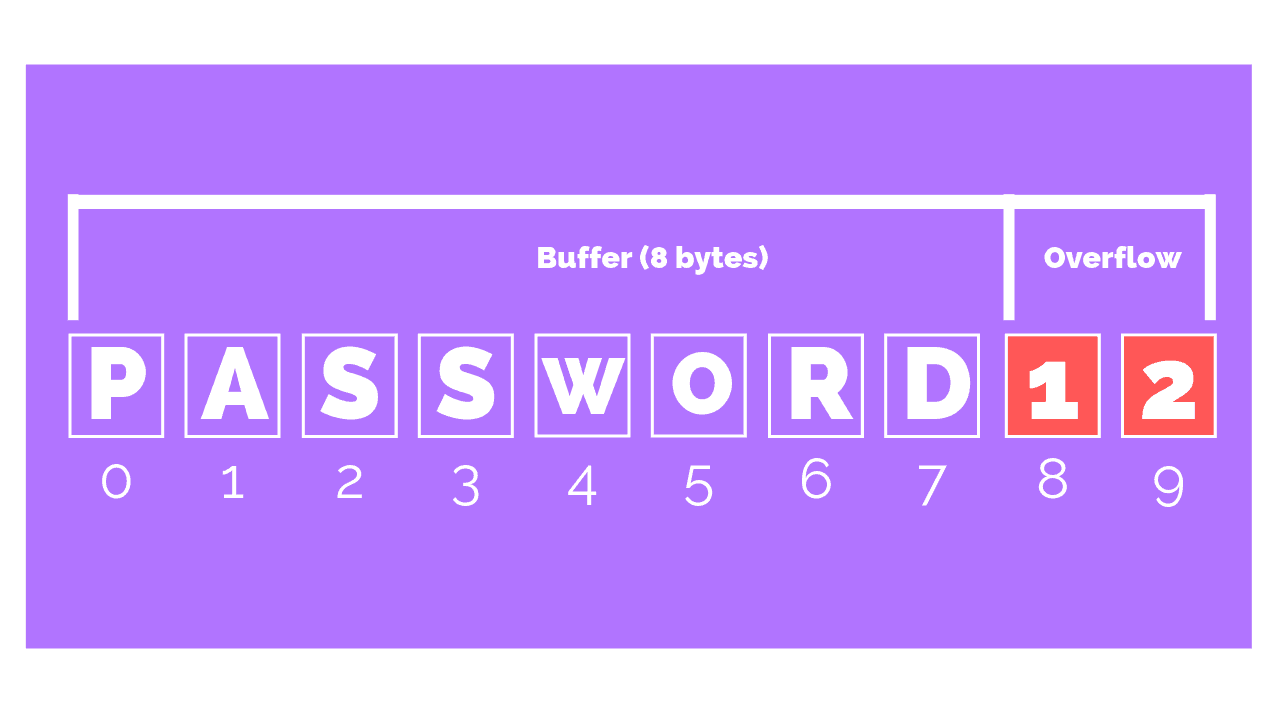
How To Prevent A Buffer Overflow Attack How do attackers exploit buffer overflows? an attacker can deliberately feed a carefully crafted input into a program that will cause the program to try and store that input in a buffer that isn’t large enough, overwriting portions of memory connected to the buffer space. A computer program may be vulnerable to buffer overflow if it handles incoming data incorrectly. anybody who can provide suitably crafted user input data may cause such a program to crash or execute arbitrary code. learn how buffer overflow attacks work and how you can avoid them. During a buffer overflow attack, the excess data overflows into the adjacent stack frame, corrupting the return address and potentially overwriting other important variables. by carefully crafting the input, attackers can manipulate the program’s execution flow and gain unauthorized access. How does buffer overflow attack work? a buffer overflow attack occurs when a program tries to fill a memory section with more data than the buffer capacity. attackers can force the application to. In this article, we will explore in detail the principles of buffer overflow and the different types of attack. we will also detail the methods of exploitation, as well as the security best practices to protect against them effectively. Buffer overflow is a common type of cyber attack that can have serious consequences for individuals and organizations. it occurs when a computer program attempts to write more data to a buffer (a temporary storage area) than it can hold, resulting in data written to adjacent memory locations.

How Do Buffer Overflow Attacks Work Kaesim During a buffer overflow attack, the excess data overflows into the adjacent stack frame, corrupting the return address and potentially overwriting other important variables. by carefully crafting the input, attackers can manipulate the program’s execution flow and gain unauthorized access. How does buffer overflow attack work? a buffer overflow attack occurs when a program tries to fill a memory section with more data than the buffer capacity. attackers can force the application to. In this article, we will explore in detail the principles of buffer overflow and the different types of attack. we will also detail the methods of exploitation, as well as the security best practices to protect against them effectively. Buffer overflow is a common type of cyber attack that can have serious consequences for individuals and organizations. it occurs when a computer program attempts to write more data to a buffer (a temporary storage area) than it can hold, resulting in data written to adjacent memory locations.

Buffer Overflow Attacks In this article, we will explore in detail the principles of buffer overflow and the different types of attack. we will also detail the methods of exploitation, as well as the security best practices to protect against them effectively. Buffer overflow is a common type of cyber attack that can have serious consequences for individuals and organizations. it occurs when a computer program attempts to write more data to a buffer (a temporary storage area) than it can hold, resulting in data written to adjacent memory locations.

Buffer Overflow Attacks Explained
Comments are closed.