Hashing Hashing Algorithms And Collisions Cryptography Practical Tls

Unit 1 Cryptography And Hashing Pdf Cryptography Public Key Hashing, hashing algorithms, and collisions cryptography practical tls. hashing, or a hashing algorithm takes "something" (a message, a file, a. Cryptographic hash functions are one way hash functions, which are infeasible to invert. the chance to find a collision (by brute force) for a strong cryptographic hash function (like sha 256) is extremely little.
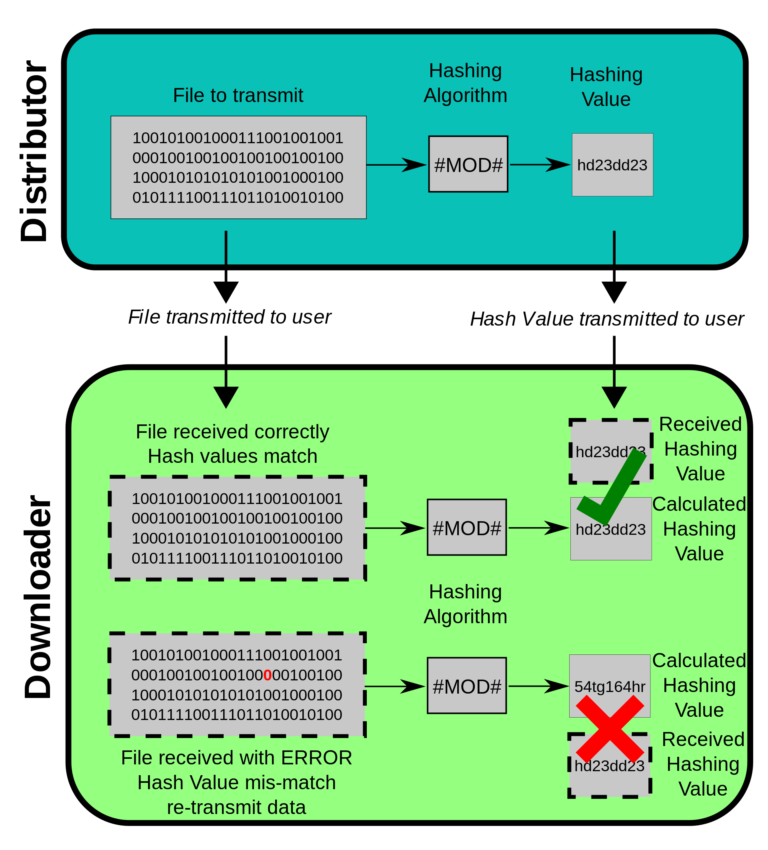
Cryptographic Hashing Algorithms Multiverse 2 357 Hashing is the process of converting any kind of data (usually passwords or installer files) into a fixed length string. there are multiple types of hashes, but for this article, we will look only at the md5 hash. md5 is an example of a hashing method. Hash collisions are an inherent mathematical property of hash functions. while they cannot be eliminated, understanding their nature and implementing proper mitigations can protect systems from practical attacks. key takeaways: a complete guide to cryptography and its role in ctf challenges. Hashing is one way. there is no “uh hashing”! system does not store actual passwords! cannot go from hash to password! why is hashing better than encryption here? does hashing protect weak, easily guessable passwords? which property is needed? weak collision resistance? let’s look at each step more detail how strong is sha 1?. This module explores hashing techniques, explaining what hashing is, its properties, and common algorithms like md5, sha, and hmac. it also covers the applications of hashing in data integrity and password protection.

Understand Hashing In Cryptography A Practical Approach Hashing is one way. there is no “uh hashing”! system does not store actual passwords! cannot go from hash to password! why is hashing better than encryption here? does hashing protect weak, easily guessable passwords? which property is needed? weak collision resistance? let’s look at each step more detail how strong is sha 1?. This module explores hashing techniques, explaining what hashing is, its properties, and common algorithms like md5, sha, and hmac. it also covers the applications of hashing in data integrity and password protection. In the symmetric key encryption based scheme shown in figure 1(a), the message and its hashcode are concatenated together to form a composite message that is then encrypted and placed on the wire. the receiver decrypts the message and separates out its hashcode, which is then compared with the hashcode calculated from the received message. the hashcode provides authentication of the document. To mitigate the risks associated with collisions, modern cryptographic practices recommend using hash functions from the sha 2 family (e.g., sha 256, sha 512) or the newer sha 3 family. these hash functions offer improved security properties and are designed to resist known cryptanalytic attacks. Hash functions take arbitrary length strings and compress them into shorter strings. the functions you studied in cs230 are examples where hashes are used to achieve o(1) lookup time in set implementations. collisions are not good for data retrieval complexity. they are disastrous in cryptographic applications. We identify a new class of transcript collision attacks on key exchange protocols that rely on efficient collision finding algorithms on the underlying hash construc tions. we implement and demonstrate concrete credential forwarding attacks on tls 1.2 client authentication, tls 1.3 server authentication, and tls channel bindings.

Understand Hashing In Cryptography A Practical Approach Hacking In the symmetric key encryption based scheme shown in figure 1(a), the message and its hashcode are concatenated together to form a composite message that is then encrypted and placed on the wire. the receiver decrypts the message and separates out its hashcode, which is then compared with the hashcode calculated from the received message. the hashcode provides authentication of the document. To mitigate the risks associated with collisions, modern cryptographic practices recommend using hash functions from the sha 2 family (e.g., sha 256, sha 512) or the newer sha 3 family. these hash functions offer improved security properties and are designed to resist known cryptanalytic attacks. Hash functions take arbitrary length strings and compress them into shorter strings. the functions you studied in cs230 are examples where hashes are used to achieve o(1) lookup time in set implementations. collisions are not good for data retrieval complexity. they are disastrous in cryptographic applications. We identify a new class of transcript collision attacks on key exchange protocols that rely on efficient collision finding algorithms on the underlying hash construc tions. we implement and demonstrate concrete credential forwarding attacks on tls 1.2 client authentication, tls 1.3 server authentication, and tls channel bindings.
Comments are closed.