Hack The Box Challenge Jeeves Walkthrough Hacking Articles
Hack The Box Challenge Jeeves Walkthrough Hacking Articles Jeeves htb guide: exploit jenkins script console for rce, gain shell access, and escalate to system using rottenpotato privilege exploit. Hackthebox is an online community where hackers and information security enthusiasts test their offensive skills by attacking vulnerable computer systems (boxes) configured by their peers. each box is a capture the flag style challenge in which the attacker must retrieve two flags hidden in text documents within the system.

Hack The Box Challenge Jeeves Walkthrough Hacking Articles Some of the concepts seem not that new and exciting, but it’s worth remembering that jeeves was the first to do them. i’ll start with a webserver and find a jenkins instance with no auth. i can abuse jenkins to get execution and remote shell. Jeeves is a medium difficulty machine on hack the box that offers an engaging learning experience. while not overly complicated, it emphasizes intriguing techniques, making it an ideal. This is a windows based machine that focuses on exploiting jenkins and also refreshed my memory on alternate data streams (ads). let’s get started! we have the ask jeeves webpage, which contains a…. Hack the box, retired machine: jeeves. this is a great ‘medium’ box that provides an opportunity for an interesting privilege escalation and the opportunity to attack jenkins!.

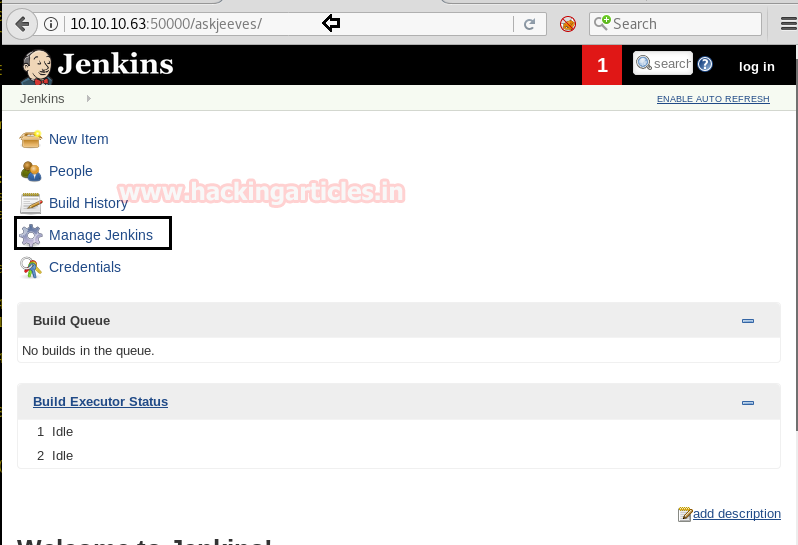
Hack The Box Challenge Jeeves Walkthrough Hacking Articles This is a windows based machine that focuses on exploiting jenkins and also refreshed my memory on alternate data streams (ads). let’s get started! we have the ask jeeves webpage, which contains a…. Hack the box, retired machine: jeeves. this is a great ‘medium’ box that provides an opportunity for an interesting privilege escalation and the opportunity to attack jenkins!. In this post we will go over a simple buffer overflow exploit with jeeves, the hackthebox pwn challenge. as this is on the easier side, techniques such as return oriented programming (rop). There are a few ways to shell this box so i’ll try and cover the main paths. this particular jenkins server didn’t require authentication to do actions against it which is a pretty big (but common) misconfiguration. jenkins has a scripting console, which you can access by going to manage jenkins => script console. This blog post is gonna walk you through jeeves that’s a medium windows machine. the initial foothold on the box is based upon the unauthenticated remote code execution on the jenkins. In this blog, we will guide you through the entire process, from initial reconnaissance to gaining root access. using key tools and techniques like nmap for port scanning, brute force directory.
Comments are closed.