Generating Keys For Encryption And Decryption

Encryption Decryption Times Elapsed For Generating Three Keys With To guarantee high data security, encryption must be unbreakable while the data remains rapidly and easily readable A novel strategy for optical encryption/decryption of information has now been What is the best encryption key management software for your business? Use our guide to compare the features of our top picks

Generating Secure Random Strong Encryption Keys Message Property How does TLS encryption and decryption work, and why is it secure? Encryption is essential for protecting data, with both symmetric and asymmetric methods offering unique advantages Encryption and Decryption Process When sending bitcoin from one address to another, private keys are utilized to decrypt the recipient’s public key, which allows the sender to access and transfer the Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses two keys—a public key for encryption and a private key for decryption
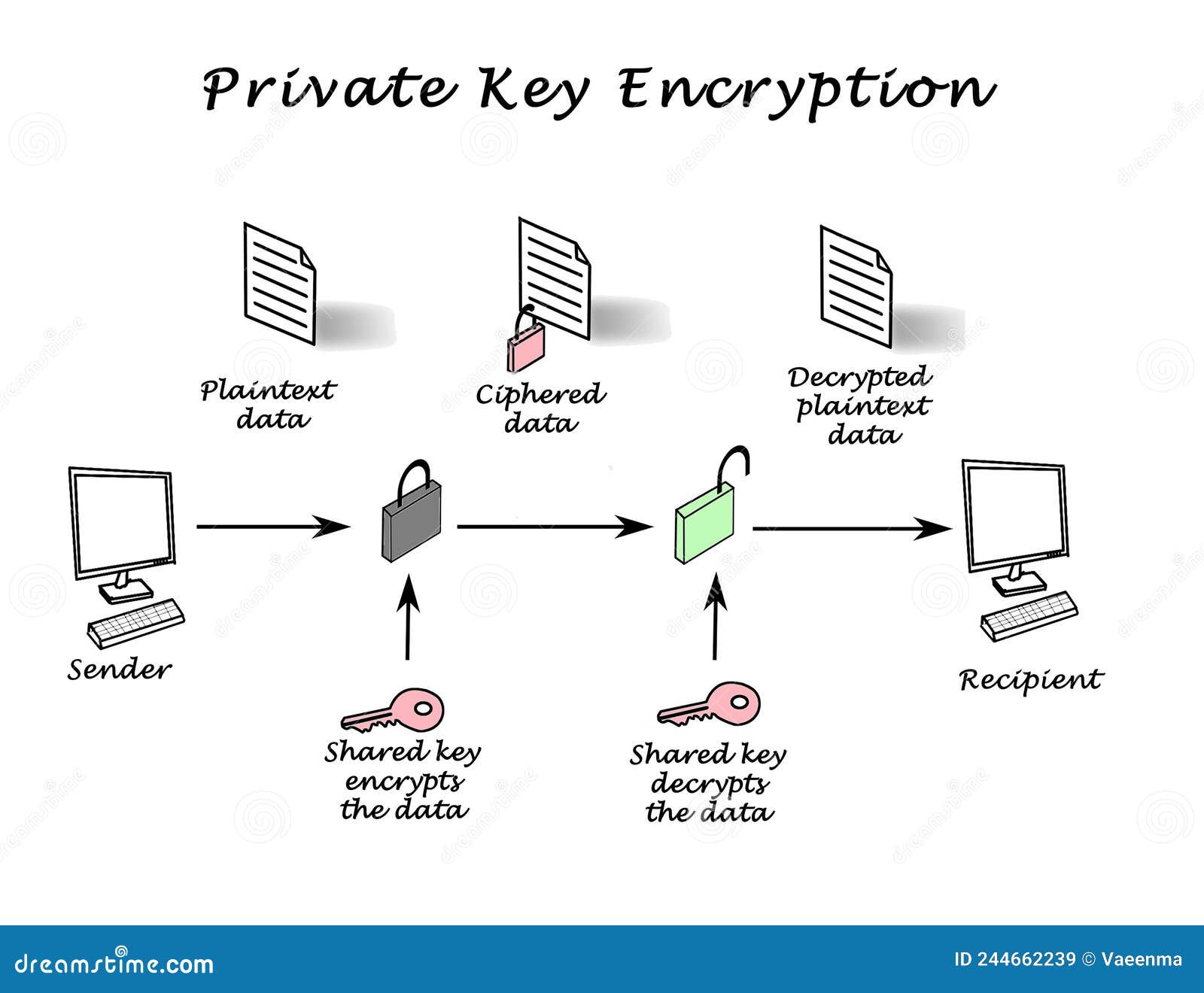
Private Key Encryption Stock Image Image Of Diagram 244662239 Encryption and Decryption Process When sending bitcoin from one address to another, private keys are utilized to decrypt the recipient’s public key, which allows the sender to access and transfer the Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses two keys—a public key for encryption and a private key for decryption A novel strategy for optical encryption/decryption of information is based on compounds with carefully modulated luminescent properties that change in response to external stimuli Asymmetric encryption uses two distinct keys for encryption and decryption To work with the code examples provided in this article, you should have Visual Studio 2022 installed in your system Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free

Process Of Generating Encryption Keys Download Scientific Diagram A novel strategy for optical encryption/decryption of information is based on compounds with carefully modulated luminescent properties that change in response to external stimuli Asymmetric encryption uses two distinct keys for encryption and decryption To work with the code examples provided in this article, you should have Visual Studio 2022 installed in your system Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free

Public Key Encryption Decryption 33 Download Scientific Diagram Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free
Comments are closed.