Exploiting More Advanced File Upload Vulnerabilities Website Hacking Penetration Testing

Web Penetration Testing Exploiting File Upload Vulnerabilities In Web Now that we know how to intercept http requests, in this lecture you will learn how to exploit a more secure file upload vulnerability and gain full control over the target web server. Welcome to this comprehensive course on website and web application hacking! in this course, you will start as a beginner with no previous knowledge about penetration testing or selection from learn website hacking penetration testing from scratch [video].
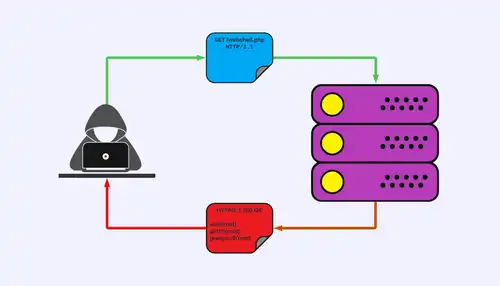
Methods For Exploiting File Upload Vulnerabilities Purplebox Topic : exploiting more advanced file upload vulnerabilitieslearn website hacking penetration testing from scratch. this course is perfect for people who ar. By understanding the full potential of file upload vulnerabilities we can achieve high severity impact that even if it’s not direct rce with a webshell, it’s still can harm a server in other. File upload vulnerabilities occur when web applications allow users to upload files without proper security controls, potentially enabling attackers to upload malicious files or execute arbitrary code on the server. Learn how to identify and hunt for advanced insecure file upload vulnerabilities using several different testing methods. read the article now!.
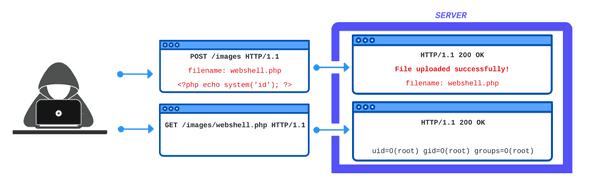
Methods For Exploiting File Upload Vulnerabilities Purplebox File upload vulnerabilities occur when web applications allow users to upload files without proper security controls, potentially enabling attackers to upload malicious files or execute arbitrary code on the server. Learn how to identify and hunt for advanced insecure file upload vulnerabilities using several different testing methods. read the article now!. File upload – this vulnerability allow attackers to upload executable files on the target web server, exploiting these vulnerabilities properly gives you full control over the target website. Upload bypass is a powerful tool designed to assist pentesters and bug hunters in testing file upload mechanisms. it leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications. File upload vulnerabilities are a powerful entry point for hackers, but they’re also a key focus for penetration testers. by using tools like weevely and burp suite, testers can simulate attacks to find and fix weaknesses before malicious hackers exploit them. File upload vulnerabilities are a critical security concern in web applications, allowing attackers to upload malicious files and execute arbitrary code. this article explores exploitation techniques, bypass methods, and mitigation strategies to secure file upload functionalities effectively.

Methods For Exploiting File Upload Vulnerabilities Purplebox File upload – this vulnerability allow attackers to upload executable files on the target web server, exploiting these vulnerabilities properly gives you full control over the target website. Upload bypass is a powerful tool designed to assist pentesters and bug hunters in testing file upload mechanisms. it leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications. File upload vulnerabilities are a powerful entry point for hackers, but they’re also a key focus for penetration testers. by using tools like weevely and burp suite, testers can simulate attacks to find and fix weaknesses before malicious hackers exploit them. File upload vulnerabilities are a critical security concern in web applications, allowing attackers to upload malicious files and execute arbitrary code. this article explores exploitation techniques, bypass methods, and mitigation strategies to secure file upload functionalities effectively.
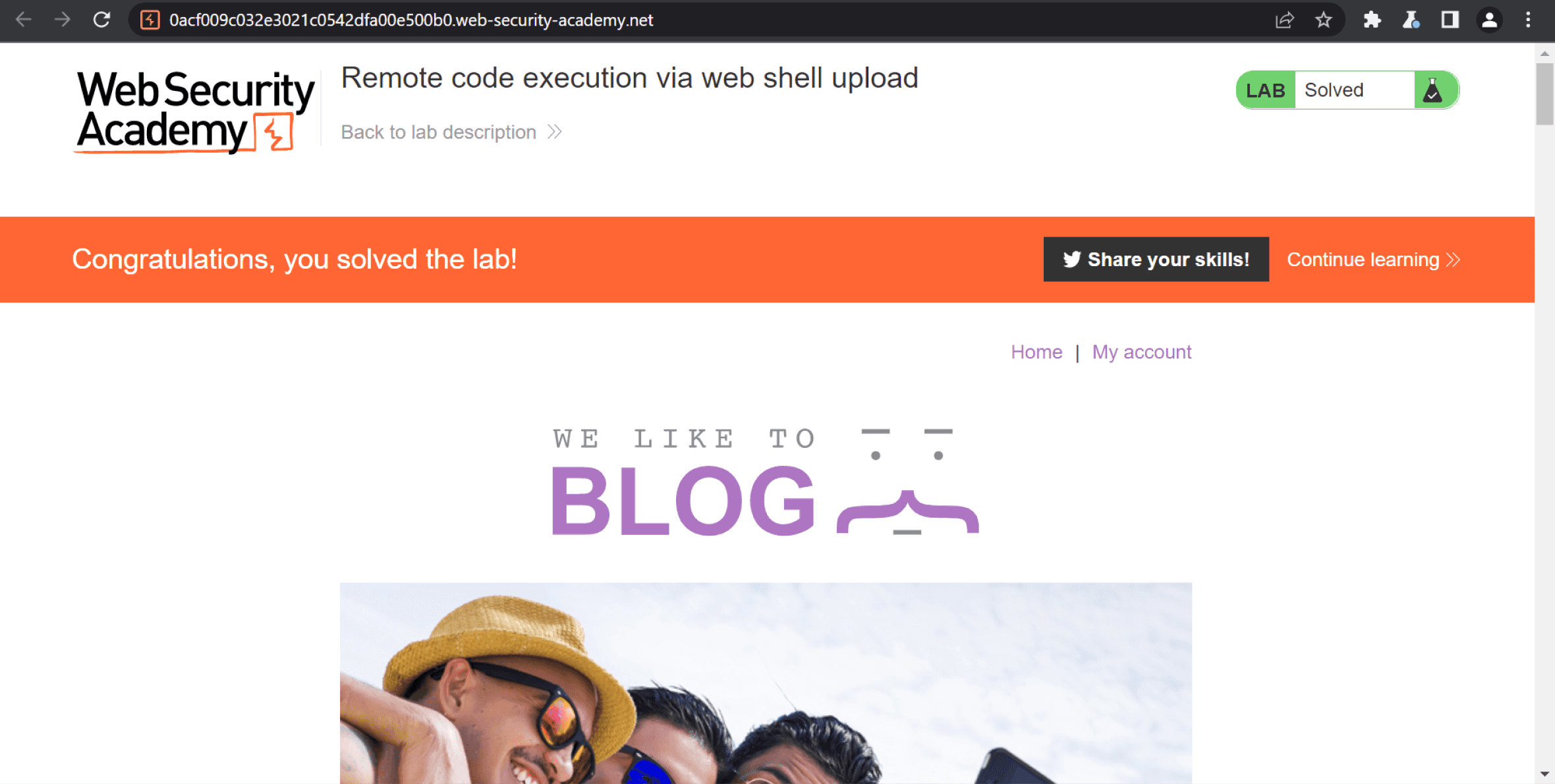
Methods For Exploiting File Upload Vulnerabilities Purplebox File upload vulnerabilities are a powerful entry point for hackers, but they’re also a key focus for penetration testers. by using tools like weevely and burp suite, testers can simulate attacks to find and fix weaknesses before malicious hackers exploit them. File upload vulnerabilities are a critical security concern in web applications, allowing attackers to upload malicious files and execute arbitrary code. this article explores exploitation techniques, bypass methods, and mitigation strategies to secure file upload functionalities effectively.
Methods For Exploiting File Upload Vulnerabilities Purplebox
Comments are closed.