Encryption Key Wrapping
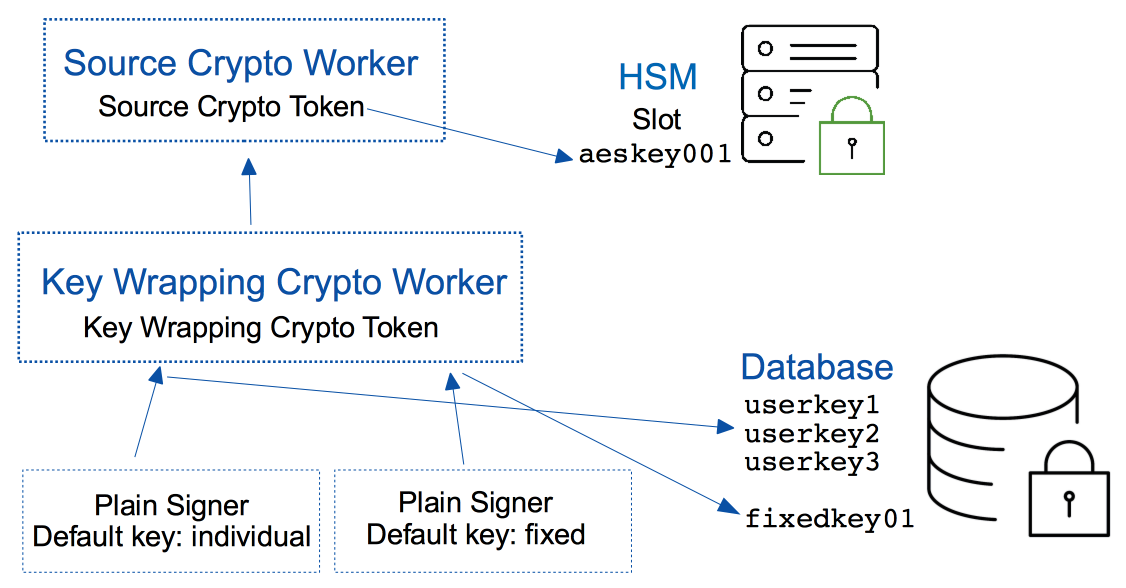
Key Wrapping In cryptography, key wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material. [1] the key wrap algorithms are intended for applications such as protecting keys while in untrusted storage or transmitting keys over untrusted communications networks. Key wrapping is a technique used in cybersecurity to protect encryption keys from unauthorized access. it involves using a symmetric encryption algorithm to wrap the key with another key, called the wrapping key, that is known only to authorized parties.

Encryption What Is Key Wrapping We can then encrypt data with a key (k 1) and which will then be wrapped to give wrap (k 1). to decrypt, we then need the kek to recover k 1. the unwrapping process also checks the. For public key encryption, we create a key pair, and then encrypt the key with our public key and which will wrap the key. to reveal the key, we can decrypt with the associated public key. In addition to describing existing methods, this publication specifies two new, deterministic authenticated encryption modes of operation of the advanced encryption standard (aes) algorithm: the aes key wrap (kw) mode and the aes key wrap with padding (kwp) mode. Key wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material. we are using these algorithms to encrypt (and authenticate) a key, using a symmetric algorithm (and symmetric key, named key encryption key).

Key Wrapping In addition to describing existing methods, this publication specifies two new, deterministic authenticated encryption modes of operation of the advanced encryption standard (aes) algorithm: the aes key wrap (kw) mode and the aes key wrap with padding (kwp) mode. Key wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material. we are using these algorithms to encrypt (and authenticate) a key, using a symmetric algorithm (and symmetric key, named key encryption key). E wrapping function is applied to an enlarged plaintext string to produce the ciphertext. each key wrap variant enlarges the plaintext by prepending a fixed string called the integrity check value (icv); for kwp ae, the enlarged plaintext also includes a 32 bit enc. The aes key wrap with padding algorithm can be used to wrap a key of any practical size with an aes key. the aes key encryption key (kek) must be 128, 192, or 256 bits. the input key data may be as short as one octet, which will result in an output of two 64 bit blocks (or 16 octets). although the aes key wrap algorithm does not place a. When the data encryption key is required, we feed in bob’s password and the salt value and unwrap the key. the unwrapped key should be the key used to encrypt the disk. The wrapping key is used to decrypt the volume key. a separate pbkdf2 transform of the volume key is also calculated and acts as a checksum, i.e. it provides a mechanism to check if the user provided the correct password.

Key Encryption All You Need To Know In One Handy Explainer E wrapping function is applied to an enlarged plaintext string to produce the ciphertext. each key wrap variant enlarges the plaintext by prepending a fixed string called the integrity check value (icv); for kwp ae, the enlarged plaintext also includes a 32 bit enc. The aes key wrap with padding algorithm can be used to wrap a key of any practical size with an aes key. the aes key encryption key (kek) must be 128, 192, or 256 bits. the input key data may be as short as one octet, which will result in an output of two 64 bit blocks (or 16 octets). although the aes key wrap algorithm does not place a. When the data encryption key is required, we feed in bob’s password and the salt value and unwrap the key. the unwrapped key should be the key used to encrypt the disk. The wrapping key is used to decrypt the volume key. a separate pbkdf2 transform of the volume key is also calculated and acts as a checksum, i.e. it provides a mechanism to check if the user provided the correct password.

Encryption Key Graphic By Zombiestudioofficial Creative Fabrica When the data encryption key is required, we feed in bob’s password and the salt value and unwrap the key. the unwrapped key should be the key used to encrypt the disk. The wrapping key is used to decrypt the volume key. a separate pbkdf2 transform of the volume key is also calculated and acts as a checksum, i.e. it provides a mechanism to check if the user provided the correct password.
Comments are closed.