Encryption And Public Keys Internet 101 Computer Science Khan

Encryption And Public Keys Internet 101 Computer Science Khan This video explains 256 bit encryption, public and private keys, ssl & tls and https. watch the next lesson: khanacademy.org computing. Mia epner, who works on security for a us national intelligence agency, explains how cryptography allows for the secure transfer of data online. this video explains 256 bit encryption, public and private keys, ssl & tls and https.

Public Key Infrastructure 101 Pdf Public Key Certificate Public As the internet grew, encryption became essential for secure communication. diffie & hellman devised a trick using one way functions to share secret keys without eavesdroppers intercepting them. Explains how cryptography allows for the secure transfer of data online. this video explains 256 bit encryption, public and private keys, ssl & tls and https. Check your understanding of cryptography and public key encryption, in this set of free practice questions designed for ap computer science principles students. Encryption is used extensively on the internet to protect sensitive information during data transmission. security protocols like ssl and tls rely on public key cryptography to encrypt data exchanged between a web browser and a website, ensuring secure browsing and online transactions.
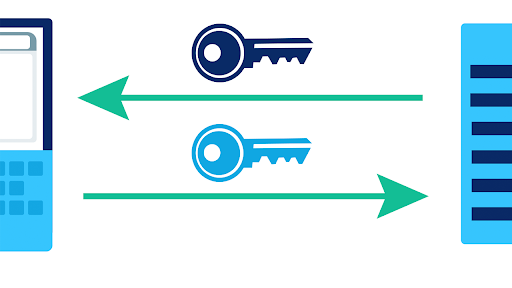
Public Key Encryption Article Khan Academy Check your understanding of cryptography and public key encryption, in this set of free practice questions designed for ap computer science principles students. Encryption is used extensively on the internet to protect sensitive information during data transmission. security protocols like ssl and tls rely on public key cryptography to encrypt data exchanged between a web browser and a website, ensuring secure browsing and online transactions. Public key encryption to the rescue! it's an asymmetric encryption technique which uses different keys for encryption and decryption, allowing computers over the internet to securely communicate with each other. let's step through the high level process of public key encryption. Mia epner, who works on security for a us national intelligence agency, explains how cryptography allows for the secure transfer of data online. this educat. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing. Asymmetric encryption, or public key cryptography, allows secure communication over open networks like the internet without the need for a pre shared secret key.
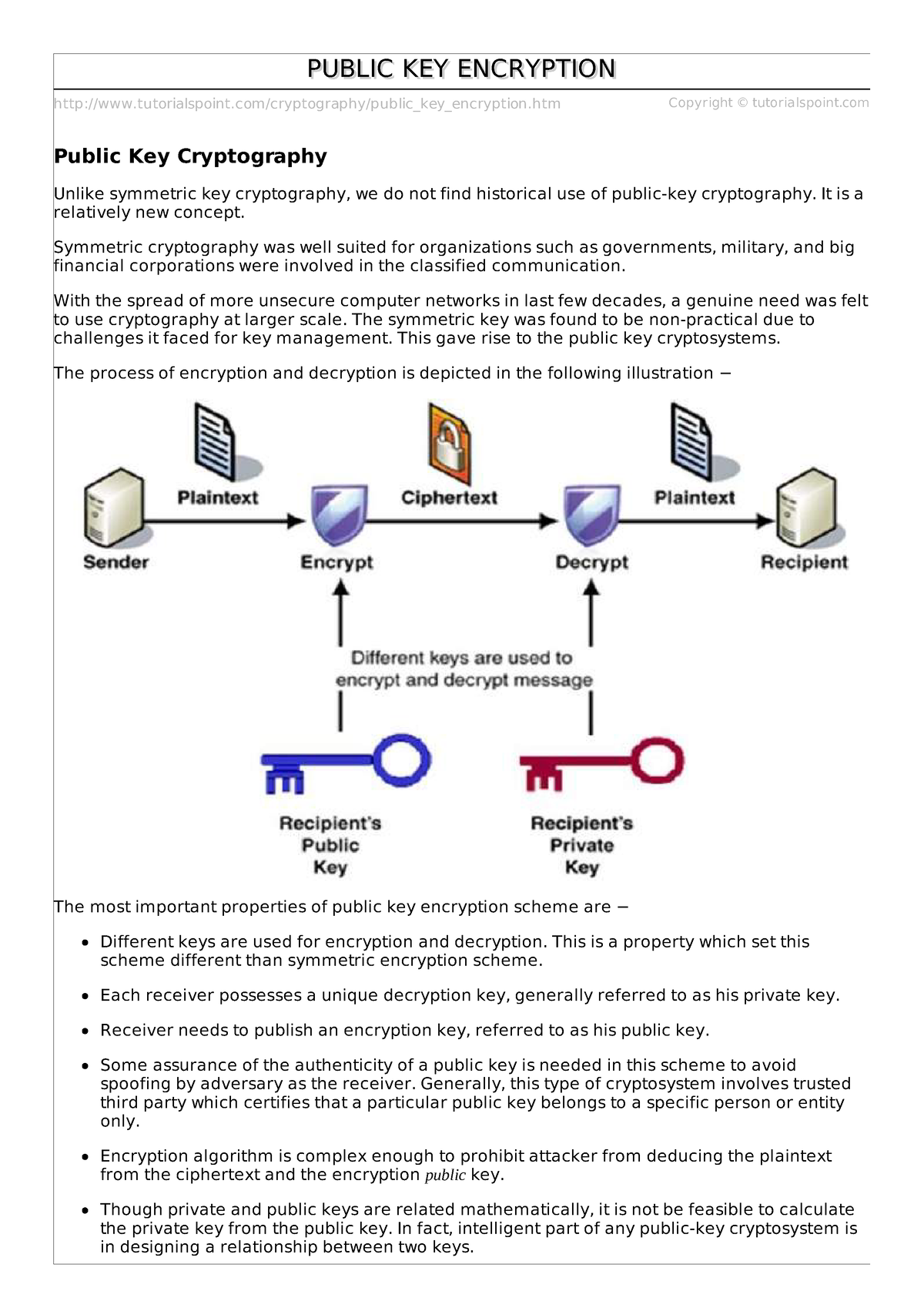
Public Key Encryption Cryptography And Network Security Notes Studocu Public key encryption to the rescue! it's an asymmetric encryption technique which uses different keys for encryption and decryption, allowing computers over the internet to securely communicate with each other. let's step through the high level process of public key encryption. Mia epner, who works on security for a us national intelligence agency, explains how cryptography allows for the secure transfer of data online. this educat. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing. Asymmetric encryption, or public key cryptography, allows secure communication over open networks like the internet without the need for a pre shared secret key.

Public Key Encryption Encryption Algorithms Encryption Cryptography Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing. Asymmetric encryption, or public key cryptography, allows secure communication over open networks like the internet without the need for a pre shared secret key.
Comments are closed.