Encryption 101 Implementation Matters

Encryption 101 Division Of Information Technology Virginia Tech Email encryption has been around for a long time—the mathematical algorithms are established. the question for businesses and their customers today is not re. The strength of modern encryption lies not just in the algorithms themselves, but in their proper implementation. according to recent security research, over 70% of encryption vulnerabilities stem from implementation flaws rather than weaknesses in the underlying cryptographic algorithms.

Best Practices For Encryption Key Management In The Cloud Discover everything you need to know about encryption, including how it works, types of encryption, its importance in digital security, and future advancements. Learn the best practices for data encryption and key management. discover how to encrypt data and ensure maximum data security. Most encryption algorithms can be implemented by many different tools. in other words, there is no single, specific program you have to use if you want to encrypt data using, say, the aes algorithm. you can choose from lots of different implementations, depending on which operating system you use. For any implementation of database encryption, the pre evaluation process is crucial. after all, there are hundreds of solutions out there, but which one do you pick? especially if you’re implementing encryption for a corporate environment, you need to be detailed to get the most bang for your buck.

Encryption Implementation Strategies Training Program For Data Most encryption algorithms can be implemented by many different tools. in other words, there is no single, specific program you have to use if you want to encrypt data using, say, the aes algorithm. you can choose from lots of different implementations, depending on which operating system you use. For any implementation of database encryption, the pre evaluation process is crucial. after all, there are hundreds of solutions out there, but which one do you pick? especially if you’re implementing encryption for a corporate environment, you need to be detailed to get the most bang for your buck. Implement data encryption effectively with practical tips on strong algorithms, key management, and real world applications to enhance cybersecurity. Encryption is important because it allows us to securely protect data that we don’t want anyone else to have access to. “the success of the information age depends on the ability to protect. Modern cryptography is based on complex mathematics, so any mistakes in the implementation of an encryption algorithm can completely void its security properties and leave your data exposed. This guide will walk through designing an encryption implementation strategy that will secure your organization’s data in the era of cloud and mobile devices in a way that is manageable, keeps complexity to a minimum, and limits impact on user productivity.
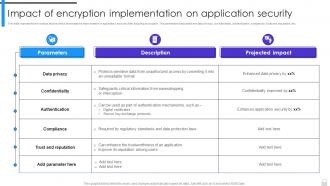
Encryption Implementation Strategies Impact Of Encryption Implement data encryption effectively with practical tips on strong algorithms, key management, and real world applications to enhance cybersecurity. Encryption is important because it allows us to securely protect data that we don’t want anyone else to have access to. “the success of the information age depends on the ability to protect. Modern cryptography is based on complex mathematics, so any mistakes in the implementation of an encryption algorithm can completely void its security properties and leave your data exposed. This guide will walk through designing an encryption implementation strategy that will secure your organization’s data in the era of cloud and mobile devices in a way that is manageable, keeps complexity to a minimum, and limits impact on user productivity.
Comments are closed.