Encrypting Data At Rest And Transit How To Protect Your Data
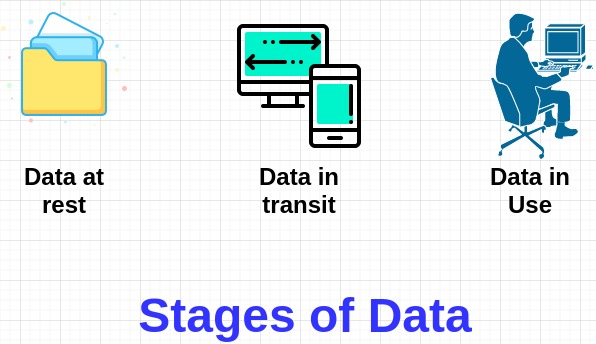
Data Encryption At Rest And In Transit Protect Your Data Cloudkul All aws services offer the ability to encrypt data at rest and in transit. aws kms integrates with the majority of services to let customers control the lifecycle of and permissions on the keys used to encrypt data on the customer’s behalf. Understanding the importance of data encryption at rest and in transit drives businesses to protect sensitive information from unauthorized access and ensure confidentiality and privacy.
Data Encryption At Rest And In Transit Protect Your Data Cloudkul Protecting sensitive data both in transit and at rest is imperative for modern enterprises as attackers find increasingly innovative ways to compromise systems and steal data. data can be exposed to risks both in transit and at rest and requires protection in both states. The first step in choosing the right encryption strategy is to understand the differences between three different states of data – in transit, at rest and in use – and the security challenges posed by each. To protect data in transit, companies should implement network security controls like firewalls and network access control. these will help secure the networks used to transmit information against malware attacks or intrusions. don’t use reactive security to protect your data. Encryption at rest: protect your local data storage units (including those used by servers and desktop & mobile clients) with a strong at rest encryption standard; ensure that the data stored in saas and cloud based services are also encrypted at rest.

Protect Data In Transit And At Rest Training Microsoft Learn To protect data in transit, companies should implement network security controls like firewalls and network access control. these will help secure the networks used to transmit information against malware attacks or intrusions. don’t use reactive security to protect your data. Encryption at rest: protect your local data storage units (including those used by servers and desktop & mobile clients) with a strong at rest encryption standard; ensure that the data stored in saas and cloud based services are also encrypted at rest. Data encryption is a fundamental aspect of data security, ensuring that sensitive information remains protected both at rest and in transit. this article delves into the intricacies of data encryption, exploring its importance, methods, and best practices for safeguarding data in various states. what is data encryption?. Here’s how to secure data during transit: encryption: always use encryption protocols such as tls (transport layer security) or ssl (secure sockets layer) for transmitting sensitive data over networks. this encrypts data during transmission, making it unreadable to unauthorized parties. By understanding encryption at rest and in transit, you've gained insight into how your data is shielded from prying eyes. remember, encryption at rest ensures that your data takes a nap in a secure fortress whenever it's not in use, while encryption in transit guards your data as it journeys from one digital stop to another. There are several methods for encrypting data at rest, each with its own strengths and weaknesses. full disk encryption (fde): this method encrypts the entire storage device, including the operating system and all files. it's a comprehensive approach that ensures all data on the device is protected.

Best Practices For Data Encryption At Rest And In Transit Data encryption is a fundamental aspect of data security, ensuring that sensitive information remains protected both at rest and in transit. this article delves into the intricacies of data encryption, exploring its importance, methods, and best practices for safeguarding data in various states. what is data encryption?. Here’s how to secure data during transit: encryption: always use encryption protocols such as tls (transport layer security) or ssl (secure sockets layer) for transmitting sensitive data over networks. this encrypts data during transmission, making it unreadable to unauthorized parties. By understanding encryption at rest and in transit, you've gained insight into how your data is shielded from prying eyes. remember, encryption at rest ensures that your data takes a nap in a secure fortress whenever it's not in use, while encryption in transit guards your data as it journeys from one digital stop to another. There are several methods for encrypting data at rest, each with its own strengths and weaknesses. full disk encryption (fde): this method encrypts the entire storage device, including the operating system and all files. it's a comprehensive approach that ensures all data on the device is protected.

How To Encrypt Data In Transit And At Rest By understanding encryption at rest and in transit, you've gained insight into how your data is shielded from prying eyes. remember, encryption at rest ensures that your data takes a nap in a secure fortress whenever it's not in use, while encryption in transit guards your data as it journeys from one digital stop to another. There are several methods for encrypting data at rest, each with its own strengths and weaknesses. full disk encryption (fde): this method encrypts the entire storage device, including the operating system and all files. it's a comprehensive approach that ensures all data on the device is protected.
Comments are closed.