Detecting Common Types Of Cybersecurity Vulnerabilities With Vulnerability Assessments

Rh Isac Detecting Common Types Of Cybersecurity Vulnerabilities With Vulnerability assessments go beyond automated scanning to help identify common vulnerabilities in your networks, applications, processes, and personnel. a vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack. Seven courses build the skills needed to perform a custom vulnerability assessment for any computer system, application or network. this type of assessment reveals how susceptible an organization is to internet intranet attacks and whether a hacker can gain access to sensitive information.
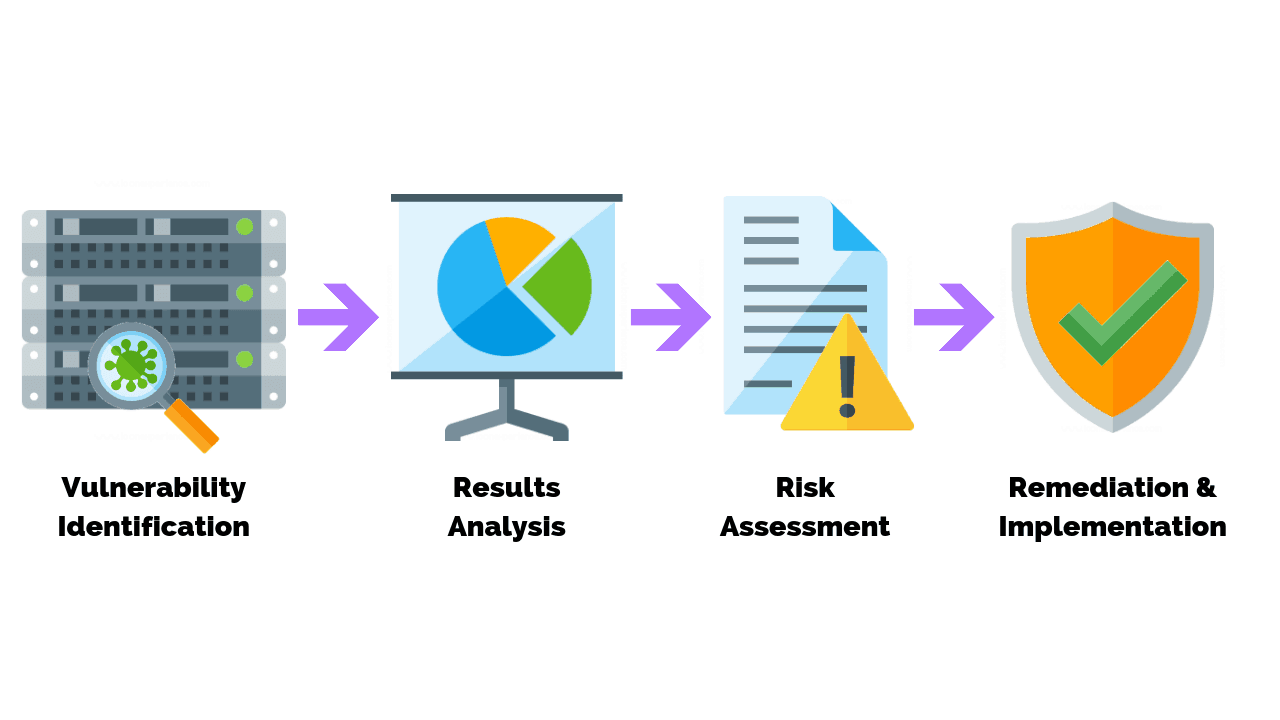
How To Conduct A Vulnerability Assessment In 8 Steps Vulnerability assessment is essentially a systematic and methodological process that allows you to identify, classify, and prioritize security weaknesses in your organization’s it infrastructure. Vulnerability assessment is a key proactive step to uncover, analyze, and remediate security weaknesses before they become breaches. in this blog, we’ll explore the core concepts of vulnerability assessment, outline the main types, and explain methodologies that organizations use to strengthen their defenses effectively. How do you perform vulnerability assessments? 1. defining and designing the testing scope. 2. identification of vulnerability. 3. analysis. 4. taking care of the weak spots. what is a vulnerability scan? 1. netsparker. 2. acunetix. 3. intruder. 4. solarwinds network vulnerability detection. 5. apptrana. 6. syxsense. 7. breachlock. This guide will discuss the vulnerability assessment types & methodologies, selection methods, advanced security measures, and tools used to better contribute to informed decision making and risk mitigation for organisations.

Instantly Grasp The Different Types Of Vulnerability Assessments With How do you perform vulnerability assessments? 1. defining and designing the testing scope. 2. identification of vulnerability. 3. analysis. 4. taking care of the weak spots. what is a vulnerability scan? 1. netsparker. 2. acunetix. 3. intruder. 4. solarwinds network vulnerability detection. 5. apptrana. 6. syxsense. 7. breachlock. This guide will discuss the vulnerability assessment types & methodologies, selection methods, advanced security measures, and tools used to better contribute to informed decision making and risk mitigation for organisations. Common types of vulnerability assessments include host vulnerability assessment, database vulnerability assessments, application vulnerability assessments, social engineering vulnerability assessments, network vulnerability assessments, and cloud security assessments. Vulnerability assessment is one of the most critical processes in identifying potential security weaknesses in a system and safeguarding against attacks. it involves systematically evaluating it systems, identifying vulnerabilities, and providing actionable steps to resolve them. There are several types of vulnerability assessments, each focusing on different aspects of an organization’s security posture. here are some of the most common types: network scans analyze network infrastructure to identify misconfigurations, outdated software, and other vulnerabilities that could be exploited by attackers. Vulnerability assessment identifies and evaluates security issues in digital systems and infrastructures that can potentially pave the way for cyber attacks. it is performed on both internal and external systems.

Instantly Grasp The Different Types Of Vulnerability Assessments With Common types of vulnerability assessments include host vulnerability assessment, database vulnerability assessments, application vulnerability assessments, social engineering vulnerability assessments, network vulnerability assessments, and cloud security assessments. Vulnerability assessment is one of the most critical processes in identifying potential security weaknesses in a system and safeguarding against attacks. it involves systematically evaluating it systems, identifying vulnerabilities, and providing actionable steps to resolve them. There are several types of vulnerability assessments, each focusing on different aspects of an organization’s security posture. here are some of the most common types: network scans analyze network infrastructure to identify misconfigurations, outdated software, and other vulnerabilities that could be exploited by attackers. Vulnerability assessment identifies and evaluates security issues in digital systems and infrastructures that can potentially pave the way for cyber attacks. it is performed on both internal and external systems.
Comments are closed.