Des Symmetric Encryption Algorithm Modern Cryptography Video Presentation

Improved Design Of Des Algorithm Based On Symmetric Encryption Des symmetric encryption algorithm | modern cryptography video presentation by angela ajos. Educational purposes only.
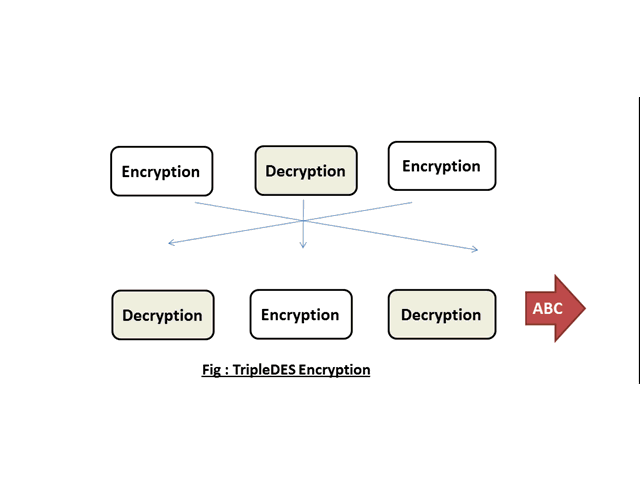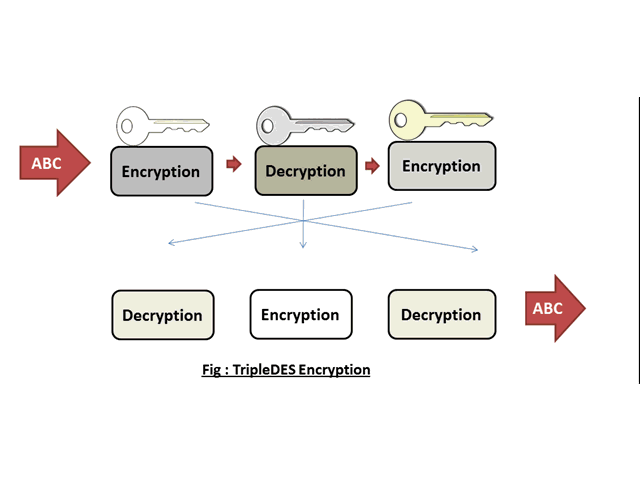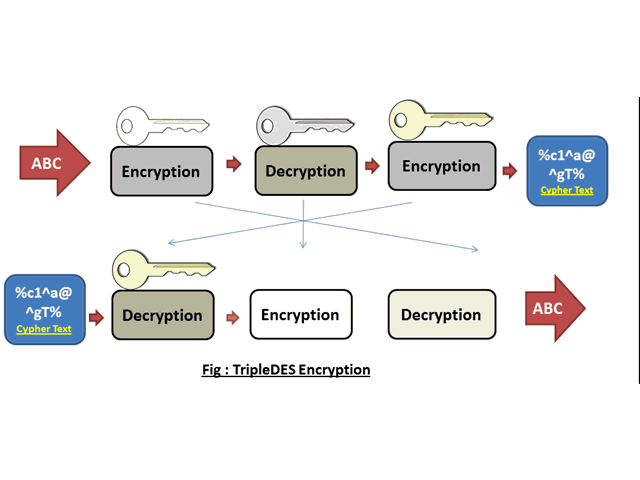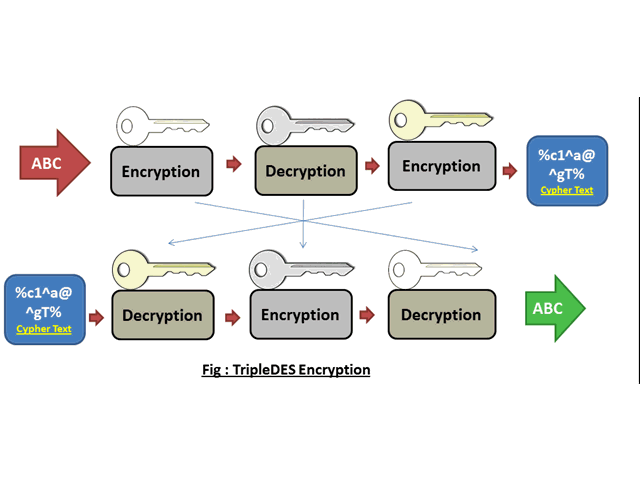
Cryptography Symmetric Encryption By Symmetric Algorithm Classes This document discusses modern symmetric key algorithms. it describes stream ciphers and block ciphers, with rc4 and des provided as examples. the concepts of confusion and diffusion are introduced. modes of operation for block ciphers are defined, including ecb, cbc, cfb and ofb. Des (data encryption standard) is a symmetric block cipher algorithm that encrypts data in 64 bit blocks using a 56 bit key. it was the first encryption standard adopted by the u.s. government for protecting sensitive unclassified federal government information. The document provides an overview of symmetric encryption algorithms, focusing on block ciphers such as des, 3des, and aes. it discusses the principles of cipher design, including the feistel structure, confusion and diffusion, and various modes of operation like ecb, cbc, and cfb. 6 1 introduction the data encryption standard (des) is a symmetric key block cipher published by the national institute of standards and technology (nist). topics discussed in this section: history overview.

Pdf A New Encryption Algorithm Using Symmetric Key Cryptography The document provides an overview of symmetric encryption algorithms, focusing on block ciphers such as des, 3des, and aes. it discusses the principles of cipher design, including the feistel structure, confusion and diffusion, and various modes of operation like ecb, cbc, and cfb. 6 1 introduction the data encryption standard (des) is a symmetric key block cipher published by the national institute of standards and technology (nist). topics discussed in this section: history overview. Cipher block chaining mode (cbc) a method to increase the security of des or any block cipher. the input to the encryption algorithm is the xor of the current plaintext block and the preceding ciphertext block. processing of a sequence of plaintext blocks is chained together. 29 (no transcript) 30 basis of cipher block chaining write a comment. Explore a history of the algorithm, including details of the structure of des. learn about the encrypt decrypt encrypt structure of 3des to extend the key. In this presentation on des data encryption standard, we learn about the origin of the encryption algorithm while understanding the importance of feistel ciphers. the steps for encryption and decryption are explained in detail, and we also read about the future of the data encryption standard. Explore the fundamentals of modern symmetric key encryption, its algorithms, and applications in securing data. learn how symmetric key encryption works.

Introduction To Modern Cryptography Lecture 2 Symmetric Encryption Cipher block chaining mode (cbc) a method to increase the security of des or any block cipher. the input to the encryption algorithm is the xor of the current plaintext block and the preceding ciphertext block. processing of a sequence of plaintext blocks is chained together. 29 (no transcript) 30 basis of cipher block chaining write a comment. Explore a history of the algorithm, including details of the structure of des. learn about the encrypt decrypt encrypt structure of 3des to extend the key. In this presentation on des data encryption standard, we learn about the origin of the encryption algorithm while understanding the importance of feistel ciphers. the steps for encryption and decryption are explained in detail, and we also read about the future of the data encryption standard. Explore the fundamentals of modern symmetric key encryption, its algorithms, and applications in securing data. learn how symmetric key encryption works.

Cryptography Simplified Symmetric Encryption Ppt In this presentation on des data encryption standard, we learn about the origin of the encryption algorithm while understanding the importance of feistel ciphers. the steps for encryption and decryption are explained in detail, and we also read about the future of the data encryption standard. Explore the fundamentals of modern symmetric key encryption, its algorithms, and applications in securing data. learn how symmetric key encryption works.

What Is A Symmetric Encryption Algorithm Twingate
Comments are closed.