Cybersecurity Architecture Five Principles To Follow And One To Avoid

Five Principles For Shaping Cybersecurity Norms Pdf Computer Cybersecurity architecture: five principles to follow (and one to avoid) ibm technology 1.21m subscribers subscribe. These are five core architecture principles to follow when designing cybersecurity systems for your organisation. create a system of security mechanisms. avoid single point of.

Five Cybersecurity Principles To Follow And One To Avoid In this article, we’ll cover 5 foundational principles to follow for building resilient cybersecurity architecture, plus one outdated mindset you should drop immediately. The principle of least privilege: cybersecurity’s essential safeguard the principle of least privilege (polp) is one of those ideas that sounds obvious once you understand it, but that’s. These are the five core architecture principles to follow when designing cybersecurity systems for your organisation. create a layered system of security mechanisms. avoid single point of. He'll begin by explaining the foundational principles of cybersecurity – five that are best practices and one that's just the opposite. the subsequent episodes will look at the various domains that apply to a well designed security architecture.

Secure Architecture Principles Pdf Superuser Access Control These are the five core architecture principles to follow when designing cybersecurity systems for your organisation. create a layered system of security mechanisms. avoid single point of. He'll begin by explaining the foundational principles of cybersecurity – five that are best practices and one that's just the opposite. the subsequent episodes will look at the various domains that apply to a well designed security architecture. This blog post outlines five key principles of cybersecurity architecture that organizations should implement to protect against cyber threats, along with one principle to avoid. Cybersecurity architecture: the design and implementation of security measures to protect an organization's information and assets (rani et al., 2022). essential for protecting against cyber threats and attacks this presentation will cover five principles to follow and one to avoid when creating a cybersecurity architectureintroduction. This ten part video series is based on a 400 level class on enterprise cybersecurity architecture taught by jeff "the security guy" crume at a local university. he'll begin by explaining the foundational principles of cybersecurity five that are best practices and one that's just the opposite. Today, we’ll dive into the whirling eddies of cryptic codes and tangled networks, armed with five trusty principles and the knowledge of a tricky misfit lurking in the shadows. our first star.

Lecture 2 Principles Of Cyber Security Download Free Pdf This blog post outlines five key principles of cybersecurity architecture that organizations should implement to protect against cyber threats, along with one principle to avoid. Cybersecurity architecture: the design and implementation of security measures to protect an organization's information and assets (rani et al., 2022). essential for protecting against cyber threats and attacks this presentation will cover five principles to follow and one to avoid when creating a cybersecurity architectureintroduction. This ten part video series is based on a 400 level class on enterprise cybersecurity architecture taught by jeff "the security guy" crume at a local university. he'll begin by explaining the foundational principles of cybersecurity five that are best practices and one that's just the opposite. Today, we’ll dive into the whirling eddies of cryptic codes and tangled networks, armed with five trusty principles and the knowledge of a tricky misfit lurking in the shadows. our first star.
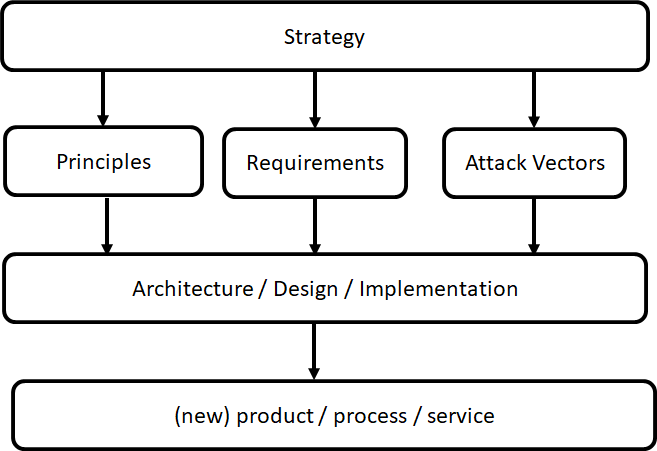
Security Principles Security Reference Architecture This ten part video series is based on a 400 level class on enterprise cybersecurity architecture taught by jeff "the security guy" crume at a local university. he'll begin by explaining the foundational principles of cybersecurity five that are best practices and one that's just the opposite. Today, we’ll dive into the whirling eddies of cryptic codes and tangled networks, armed with five trusty principles and the knowledge of a tricky misfit lurking in the shadows. our first star.

Eric Vermeer On Linkedin Cybersecurity Architecture Five Principles
Comments are closed.