Combination Of Secret Key Encryption Public Key Encryption And A

12 Combination Of Secret Key Encryption Public Key Encryption And A In a public key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. Public key cryptography provides a secure way to exchange information and authenticate users by using pairs of keys. the public key is used for encryption and signature verification, while the private key is used for decryption and signing.

12 Combination Of Secret Key Encryption Public Key Encryption And A Public key encryption enables parties to initiate secure communications through an open medium, such as the internet, in which there might be eavesdroppers. public key encryption is not considered a secure method of communication because a public key can be intercepted. Diffie–hellman key exchange allows two parties to jointly establish a shared secret key over an insecure communication channel the established key can then be used to encrypt subsequent communication using a symmetric key cipher “new directions in cryptography” by whitfield diffie and martin hellman, 1976 based on the discrete logarithm. This article delves into the intricacies of how public and private key encryption works, exploring its underlying mathematical principles, common algorithms, real world applications, and security considerations. Modern secret key cryptography messages encrypted and decrypted with a shared secret key usually the same key for both operations ("symmetric").

Combination Of Secret Key Encryption Public Key Encryption And A This article delves into the intricacies of how public and private key encryption works, exploring its underlying mathematical principles, common algorithms, real world applications, and security considerations. Modern secret key cryptography messages encrypted and decrypted with a shared secret key usually the same key for both operations ("symmetric"). Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures. Surprisingly, this can be done using a technology called public key encryption. the basic idea of public key encryption is that the receiver, bob in this case, runs a key gener ation algorithm g, obtaining a pair of keys: (pk,sk) ←rg(). the key pk is bob’s public key, and sk is bob’s secret key. The most commonly used implementations of public key cryptography (also known as public key encryption and asymmetric encryption) are based on algorithms presented by rivest shamir adelman (rsa) data security. Unlike traditional encryption methods, it uses two keys: a public key for encryption and a private key for decryption, eliminating the need for shared secrets. in this article, we’ll explore the principles of public key cryptography, its key components, and real world applications.
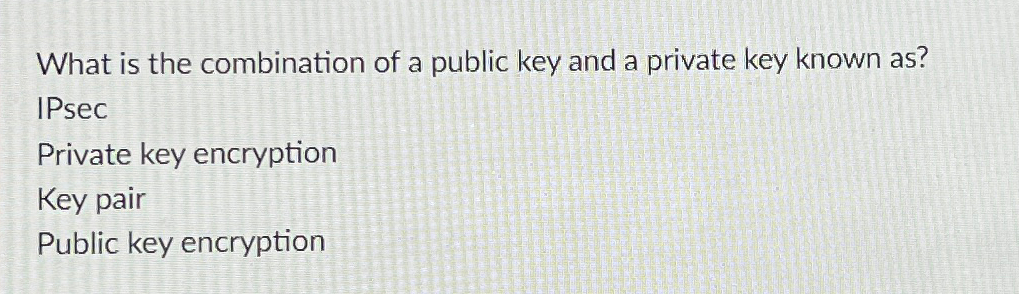
Solved What Is The Combination Of A Public Key And A Private Chegg Asymmetric cryptography refers to using both a public key and a private key. the public key is known to everyone and is used to encrypt messages and verify digital signatures. the private key is known only to the user and is used to decrypt the ciphertext or generate digital signatures. Surprisingly, this can be done using a technology called public key encryption. the basic idea of public key encryption is that the receiver, bob in this case, runs a key gener ation algorithm g, obtaining a pair of keys: (pk,sk) ←rg(). the key pk is bob’s public key, and sk is bob’s secret key. The most commonly used implementations of public key cryptography (also known as public key encryption and asymmetric encryption) are based on algorithms presented by rivest shamir adelman (rsa) data security. Unlike traditional encryption methods, it uses two keys: a public key for encryption and a private key for decryption, eliminating the need for shared secrets. in this article, we’ll explore the principles of public key cryptography, its key components, and real world applications.
Comments are closed.