Asymmetric Encryption Simply Explained
Asymetric Encryption Simply Explained How does public key cryptography work? what is a private key and a public key? why is asymmetric encryption different from symmetric encryption? i'll explain all of these in plain. Asymmetric encryption, also known as public key cryptography, is a type of encryption that uses a pair of keys to encrypt and decrypt data. the pair of keys includes a public key, which can be shared with anyone, and a private key, which is kept secret by the owner.

Asymmetric Encryption Network Encyclopedia Asymmetric encryption is an encryption method that uses two different keys—a public key and a private key—to encrypt and decrypt data. it’s generally regarded as more secure, though less efficient, than symmetric encryption. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys one public key and one private key to encrypt and decrypt a message and protect it from unauthorized access or use. Asymmetric encryption, also known as public key cryptography, is an example of one type. unlike “normal” (symmetric) encryption, asymmetric encryption encrypts and decrypts the data using two separate yet mathematically connected cryptographic keys. Asymmetric encryption, also known as public key encryption, uses a public key private key pairing: data encrypted with the public key can only be decrypted with the private key. tls (or ssl), the protocol that makes https possible, relies partially on asymmetric encryption.

Asymmetric Encryption Klye Projects Blog Asymmetric encryption, also known as public key cryptography, is an example of one type. unlike “normal” (symmetric) encryption, asymmetric encryption encrypts and decrypts the data using two separate yet mathematically connected cryptographic keys. Asymmetric encryption, also known as public key encryption, uses a public key private key pairing: data encrypted with the public key can only be decrypted with the private key. tls (or ssl), the protocol that makes https possible, relies partially on asymmetric encryption. What is asymmetric encryption? encryption is a method used to scramble information to make it unreadable or unusable. with normal (symmetric) encryption, the same key used by the sender to encrypt (scramble) the data is used by the recipient to decrypt (unscramble) it. Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys. you need to send a message across the internet, but you don't want anyone but the intended recipient to see what you've written. asymmetric encryption can help you achieve that goal. Asymmetric encryption, also known as public key cryptography, is an essential concept in modern information security. this beginner’s guide will introduce asymmetric encryption and how it works. Learn how asymmetric encryption secures digital communication with public private keys, rsa, and ecc, plus real world examples.
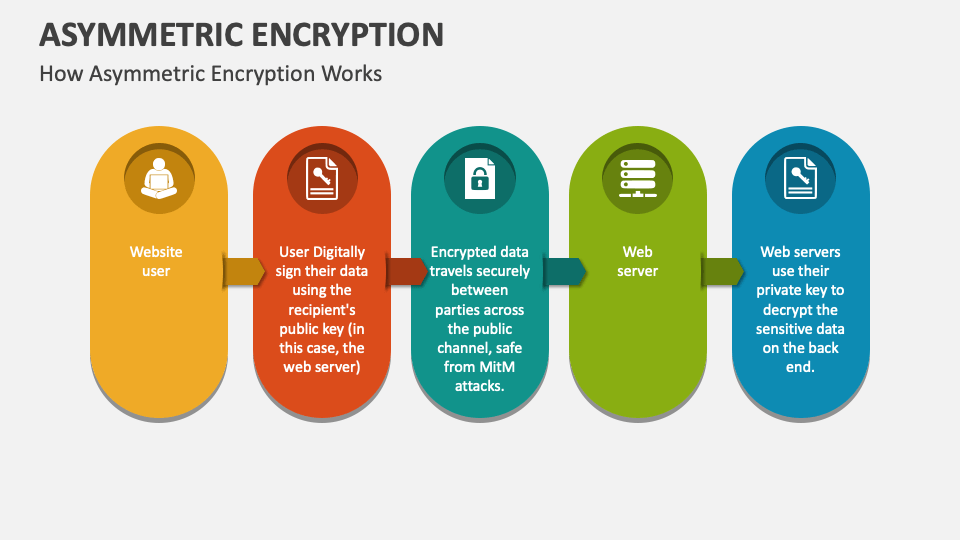
Asymmetric Encryption Powerpoint And Google Slides Template Ppt Slides What is asymmetric encryption? encryption is a method used to scramble information to make it unreadable or unusable. with normal (symmetric) encryption, the same key used by the sender to encrypt (scramble) the data is used by the recipient to decrypt (unscramble) it. Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using shared keys. you need to send a message across the internet, but you don't want anyone but the intended recipient to see what you've written. asymmetric encryption can help you achieve that goal. Asymmetric encryption, also known as public key cryptography, is an essential concept in modern information security. this beginner’s guide will introduce asymmetric encryption and how it works. Learn how asymmetric encryption secures digital communication with public private keys, rsa, and ecc, plus real world examples.

Asymmetric Encryption Method Advantages And Disadvantages Electrodummies Asymmetric encryption, also known as public key cryptography, is an essential concept in modern information security. this beginner’s guide will introduce asymmetric encryption and how it works. Learn how asymmetric encryption secures digital communication with public private keys, rsa, and ecc, plus real world examples.
Symmetric And Asymmetric Encryption The Difference Explained
Comments are closed.