Api Authentication Jwt Oauth2 And More

Api Authentication Jwt Vs Oauth R Devto Need to secure your api? here's a breakdown of the top 7 authentication methods, their use cases, and strengths: oauth 2.0: ideal for third party integrations. uses tokens for secure, delegated access. api keys: simple and easy for internal services but less secure without proper management. Understanding the principles, use cases, and implementation of authentication methods ranging from basic auth to oauth2 and jwt helps developers choose the right approach to ensure the security and reliability of apis.
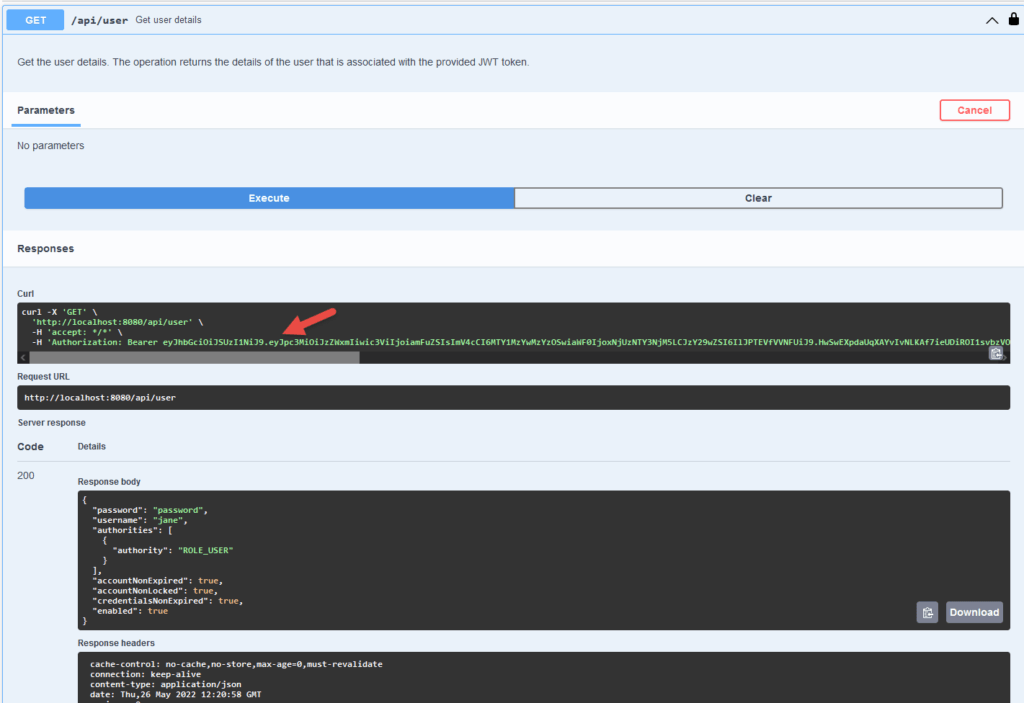
Configure Jwt Authentication For Openapi Baeldung In this video, we dive into api authentication, covering why it’s essential, how it secures api access, and four common methods: basic authentication, api key authentication, jwt. Jwt is often used in conjunction with other protocols and technologies, such as oauth and openid connect, to provide a complete authentication and authorization solution. In this article, we'll break down oauth and jwt, explaining how each works, pointing out the key differences, and sharing best practices for implementing each separately or together. In this post, i’ll walk you through the most common authentication methods used by apis today, from the simplest approach to more advanced techniques. don’t worry if you’re new to this — i’ll.
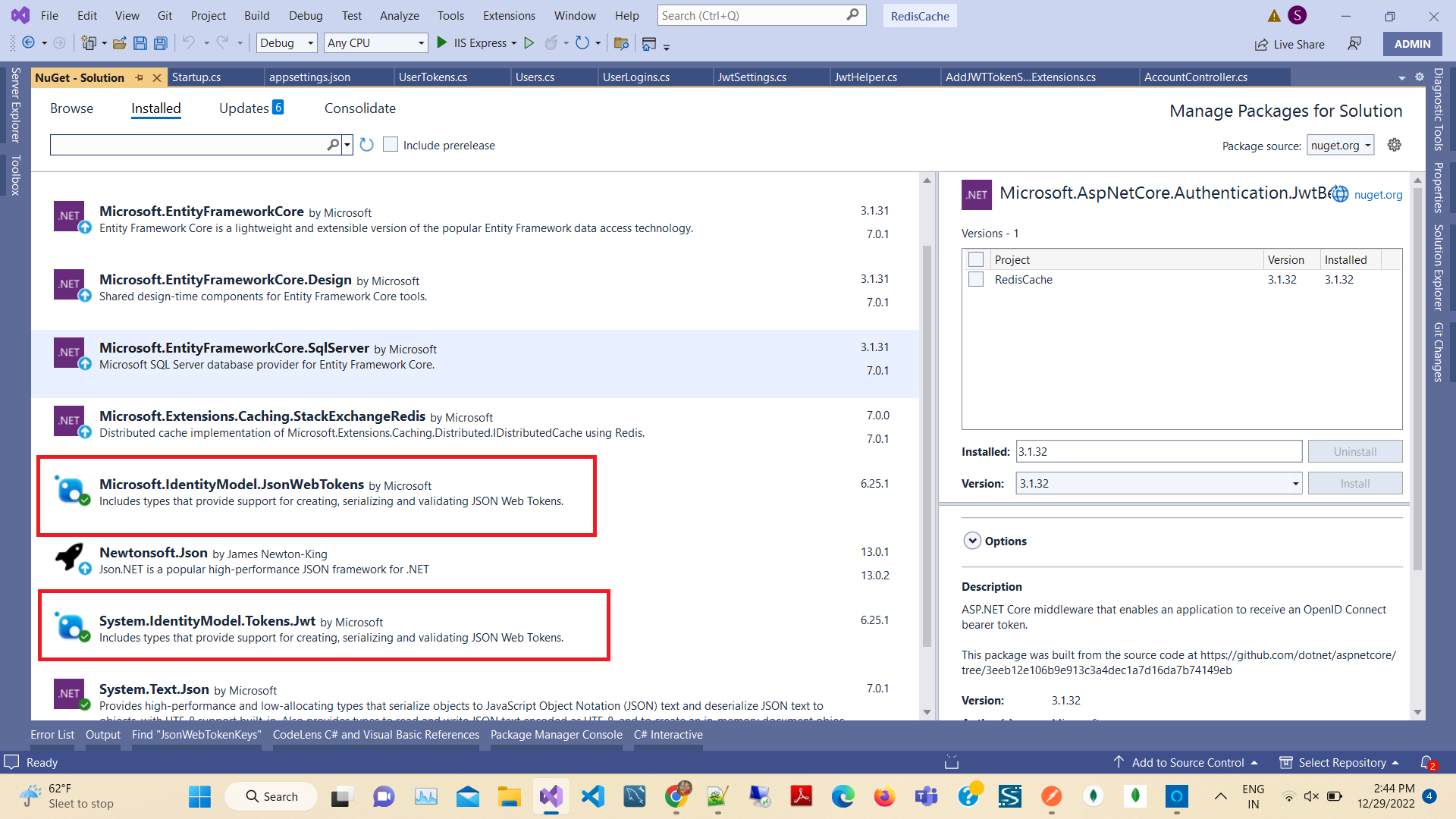
Jwt Token Authentication And Authorizations In Web Api Code2night In this article, we'll break down oauth and jwt, explaining how each works, pointing out the key differences, and sharing best practices for implementing each separately or together. In this post, i’ll walk you through the most common authentication methods used by apis today, from the simplest approach to more advanced techniques. don’t worry if you’re new to this — i’ll. Compare oauth and jwt to understand their differences, use cases, & how they enable secure authentication and authorization for applications. When it comes to api authentication, the debate between oauth 2.0 and jwt (json web tokens) is as heated as the one between tacos and burritos. as a seasoned software engineer and content creator, i've wrestled with this question more times than i can count. Explore various api authentication methods, their pros and cons, and find the right fit for your security and scalability needs. Learn how to handle various authentication methods in rest assured for secure api testing. discover practical examples for oauth, jwt, and more, integrated with top automation testing tools. explore best practices for securing your api tests and managing authentication tokens.
Github Nicolaslinares Oauth2 And Jwt Authentication Oauth 2 0 And Compare oauth and jwt to understand their differences, use cases, & how they enable secure authentication and authorization for applications. When it comes to api authentication, the debate between oauth 2.0 and jwt (json web tokens) is as heated as the one between tacos and burritos. as a seasoned software engineer and content creator, i've wrestled with this question more times than i can count. Explore various api authentication methods, their pros and cons, and find the right fit for your security and scalability needs. Learn how to handle various authentication methods in rest assured for secure api testing. discover practical examples for oauth, jwt, and more, integrated with top automation testing tools. explore best practices for securing your api tests and managing authentication tokens.
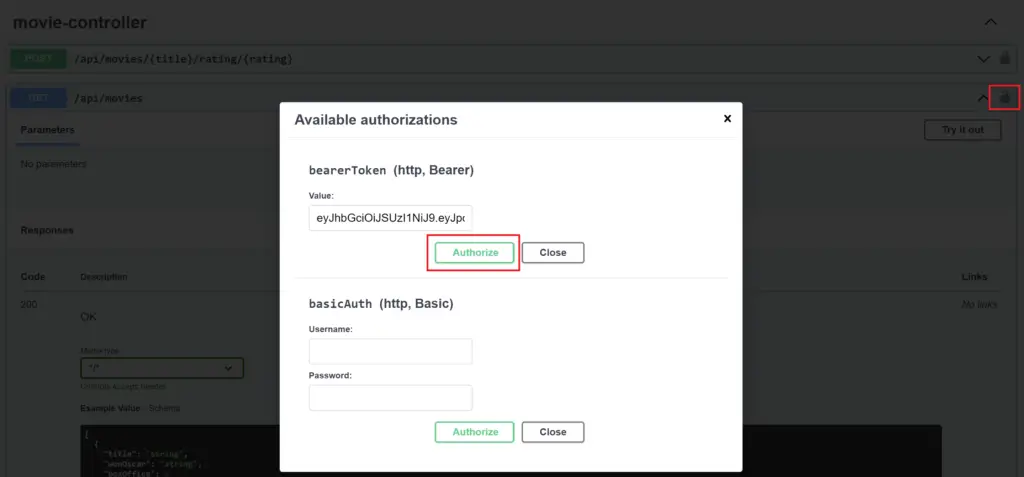
How To Configure Openapi 3 Spec With Basic Jwt Authentication Java Explore various api authentication methods, their pros and cons, and find the right fit for your security and scalability needs. Learn how to handle various authentication methods in rest assured for secure api testing. discover practical examples for oauth, jwt, and more, integrated with top automation testing tools. explore best practices for securing your api tests and managing authentication tokens.

Oauth Jwt Authentication And Authorization Schema Information
Comments are closed.