Anti Flag Easy Hackthebox Reversing Challenge Binary Patching With Ghidra Pwntools

Sekure Decrypt Easy Hackthebox Reversing Challenge Walkthrough R Video walkthrough for retired hackthebox (htb) reversing challenge "anti flag" [easy]: "flag? what's a flag?" includes binary patching with ghidra pwntools! hope you enjoy. He also provides a few other ways to solve the challenge by patching the binary using both ghidra and pwntools. i had to lean a lot on his walk throughs as i am definitely still learning.

Templed Hackthebox Challenge The Dutch Hacker We can use ghidra to open the binary and start reverse engineering our way to better understand how the binary works. after displaying the banner, the binary runs a loop from 0 to 0x1c. In ghidra, we notice some mismatch between the assembly code and the disassembled one. we solve this by unchecking eliminate unreachable code under edit tool options, and we find that there is a condition that is never met in the following function:. In a simple sentence, patching a program is when you can modify the program binary so the program behaves differently, for instance, skipping authentication logic by bypassing the compare. Let's analysis the binary in binaryninja. look at the main function. this program use ptrace syscall, that means while the program being traced, the program will be stop. when the program is traced, it print "well done!!" and exit the program. otherwise it compare something. so we can't debug or trace the program with gdb.
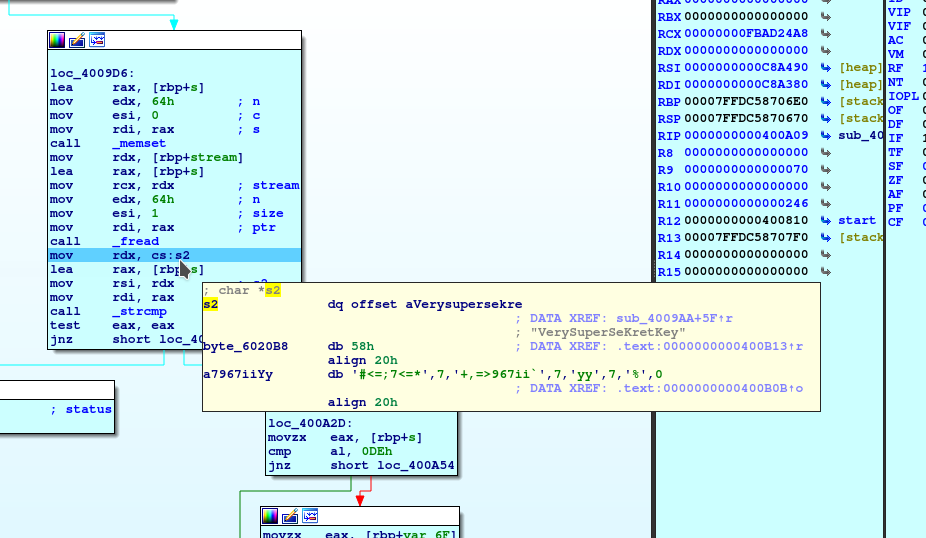
Hackthebox Find The Secret Flag Reversing Challenge In a simple sentence, patching a program is when you can modify the program binary so the program behaves differently, for instance, skipping authentication logic by bypassing the compare. Let's analysis the binary in binaryninja. look at the main function. this program use ptrace syscall, that means while the program being traced, the program will be stop. when the program is traced, it print "well done!!" and exit the program. otherwise it compare something. so we can't debug or trace the program with gdb. 135k subscribers in the reverseengineering community. a moderated community dedicated to all things reverse engineering. The anti flag challenge on hack the box is an easy level reverse engineering challenge where participants analyze and modify a binary to uncover the hidden flag. the solution involves using tools like xxd to examine the binary’s hexadecimal structure, patching specific byte sequences, and reconstructing the modified binary. Anti flag is an easy reversing challenge on hack the box. the description is "flag? what's a flag?" this one has some fun anti debugger ltrace elements in it. i first run the program with nothing attached to it and i get this back. running it with "ltrace" gives me a different response. let's open this up…. The article provides a detailed walkthrough of the hackthebox "flag casino" challenge, which involves reverse engineering a binary file to extract a hidden flag.
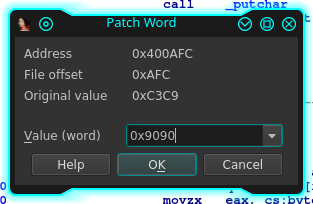
Hackthebox Find The Secret Flag Reversing Challenge 135k subscribers in the reverseengineering community. a moderated community dedicated to all things reverse engineering. The anti flag challenge on hack the box is an easy level reverse engineering challenge where participants analyze and modify a binary to uncover the hidden flag. the solution involves using tools like xxd to examine the binary’s hexadecimal structure, patching specific byte sequences, and reconstructing the modified binary. Anti flag is an easy reversing challenge on hack the box. the description is "flag? what's a flag?" this one has some fun anti debugger ltrace elements in it. i first run the program with nothing attached to it and i get this back. running it with "ltrace" gives me a different response. let's open this up…. The article provides a detailed walkthrough of the hackthebox "flag casino" challenge, which involves reverse engineering a binary file to extract a hidden flag.
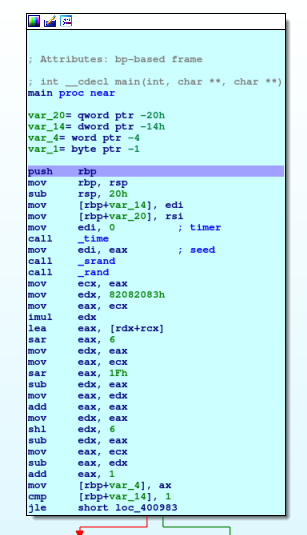
Hackthebox Find The Secret Flag Reversing Challenge Anti flag is an easy reversing challenge on hack the box. the description is "flag? what's a flag?" this one has some fun anti debugger ltrace elements in it. i first run the program with nothing attached to it and i get this back. running it with "ltrace" gives me a different response. let's open this up…. The article provides a detailed walkthrough of the hackthebox "flag casino" challenge, which involves reverse engineering a binary file to extract a hidden flag.
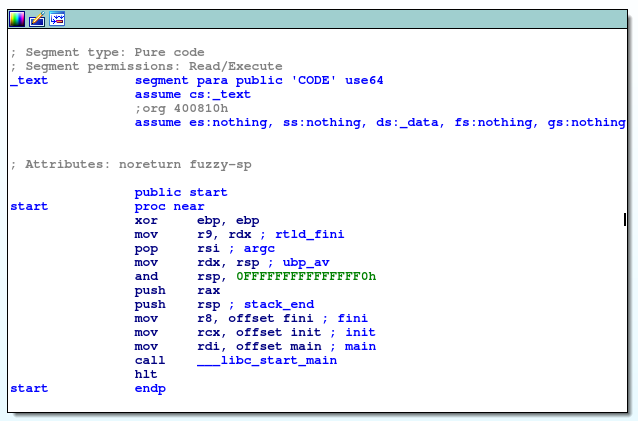
Hackthebox Find The Secret Flag Reversing Challenge
Comments are closed.