A Reliable Secret Key Algorithm For Encryption And
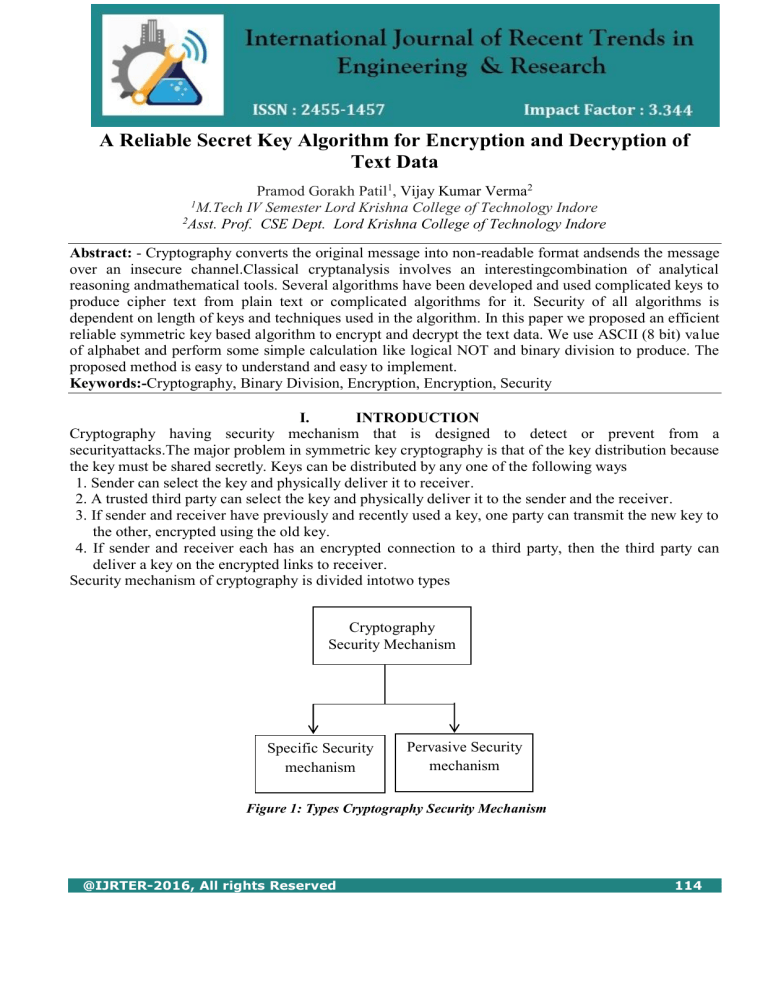
A Reliable Secret Key Algorithm For Encryption And Explore secret key cryptography, covering essential methods, key management challenges, and best practices to safeguard data and enhance security in organizational applications. Secret key algorithms are basically used in the places where that needs to encrypt lot of data. there are about hundreds of different symmetric key algorithms. in this article i’ll.

Public Key Private Key Encryption Algorithm Adventure Gold In this paper we proposed an efficient reliable symmetric key based algorithm to encrypt and decrypt the text data. we use ascii (8 bit) value of alphabet and perform some simple calculation like logical not and binary division to produce. the proposed method is easy to understand and easy to implement. Take a deep dive into the various symmetric key encryption algorithms, from the antiquated data encryption standard, or des, to its replacement advanced encryption standard, or aes. easttom offers an in depth look at the math behind symmetric key algorithms, as well as their variants, from triple des to rc4 (rivest cipher 4) to skipjack. Here are some of the common secrete key algorithms that are used for encryption and decryption. des is one of the most popular symmetric encryption algorithms out there. it is a block. Public key algorithms are based on simple operations on bit patterns. the purpose of the dss algorithm is to enable two users to securely reach agreement about a shared secret that can be used as a secret key for subsequent symmetric encryption of messages.

Encryption Algorithm Understanding 5 Types Of Encryption Algorithm Here are some of the common secrete key algorithms that are used for encryption and decryption. des is one of the most popular symmetric encryption algorithms out there. it is a block. Public key algorithms are based on simple operations on bit patterns. the purpose of the dss algorithm is to enable two users to securely reach agreement about a shared secret that can be used as a secret key for subsequent symmetric encryption of messages. There are two types of key based encryption algorithms, symmetric encryption algorithms (secret key algorithms) and asymmetric encryption algorithms (or public key algorithms). symmetric encryption examples include aes (advance encryption standard), triple des, twofish and blowfish algorithms and rsa is a type of asymmetric algorithm. Secret key cryptography, also known as symmetric key cryptography, is a type of encryption where a single secret key is used for both encryption and decryption of a message. Secret key algorithms are fundamental to symmetric key cryptography, where a single key is used for both encryption and decryption. common examples include the data encryption standard (des) and the advanced encryption standard (aes). In secret key cryptography, two (or more) parties share the same key, and that key is used to encrypt and decrypt data. as the name implies, secret key cryptography relies on keeping the key secret. if the key is compromised, the security offered by cryptography is severely reduced or eliminated.

Rsa Public Key Encryption Algorithm Blockychain Medium There are two types of key based encryption algorithms, symmetric encryption algorithms (secret key algorithms) and asymmetric encryption algorithms (or public key algorithms). symmetric encryption examples include aes (advance encryption standard), triple des, twofish and blowfish algorithms and rsa is a type of asymmetric algorithm. Secret key cryptography, also known as symmetric key cryptography, is a type of encryption where a single secret key is used for both encryption and decryption of a message. Secret key algorithms are fundamental to symmetric key cryptography, where a single key is used for both encryption and decryption. common examples include the data encryption standard (des) and the advanced encryption standard (aes). In secret key cryptography, two (or more) parties share the same key, and that key is used to encrypt and decrypt data. as the name implies, secret key cryptography relies on keeping the key secret. if the key is compromised, the security offered by cryptography is severely reduced or eliminated.

Presentation Of Public Key Cryptography Algorithm For Information Secret key algorithms are fundamental to symmetric key cryptography, where a single key is used for both encryption and decryption. common examples include the data encryption standard (des) and the advanced encryption standard (aes). In secret key cryptography, two (or more) parties share the same key, and that key is used to encrypt and decrypt data. as the name implies, secret key cryptography relies on keeping the key secret. if the key is compromised, the security offered by cryptography is severely reduced or eliminated.
Comments are closed.