A Data Cloud Of Closed Protected Data Unlocked By Password Keys

A Data Cloud Of Closed Protected Data Unlocked By Password Keys Secure a cloud environment by implementing encryption for data at rest and in transit, enforcing strict access control policies, maintaining regulatory compliance, performing regular audits, and using ai for threat detection. Cloud encryption is defined as the process of encoding and transforming data before transferring it to the cloud. this process converts plaintext data into ciphertext using mathematical algorithms and makes the data unreadable, thus protecting it from unauthorized and potentially malicious users.

An Approach To Access Encrypted Cloud Databases Pdf Databases Data encryption involves the use of complex mathematical algorithms and digital keys to protect sensitive data. learn about the various methods used. Cloud storage always encrypts your data on the server side, before it is written to disk, at no additional charge. besides this standard, cloud storage behavior, there are additional ways to. Azure key vault helps safeguard cryptographic keys and secrets that cloud applications and services use. key vault streamlines the key management process and enables you to maintain control of keys that access and encrypt your data. developers can create keys for development and testing in minutes, and then migrate them to production keys. Cloud encryption is a security method that converts data (text file code image) into unreadable ciphertext using cryptographic algorithms. this helps ensure that even if the data is intercepted or breached, it remains secure and confidential. cloud encryption protects data against unauthorized access in three states:.

Your Data Their Cloud Bring Your Own Encryption Keys Azure key vault helps safeguard cryptographic keys and secrets that cloud applications and services use. key vault streamlines the key management process and enables you to maintain control of keys that access and encrypt your data. developers can create keys for development and testing in minutes, and then migrate them to production keys. Cloud encryption is a security method that converts data (text file code image) into unreadable ciphertext using cryptographic algorithms. this helps ensure that even if the data is intercepted or breached, it remains secure and confidential. cloud encryption protects data against unauthorized access in three states:. Data in the cloud is encrypted using algorithms to convert it into unreadable ciphertext, accessible only with decryption keys. the role of data encryption is critical in maintaining the safety and confidentiality of information housed in the cloud. Using vulnerability exploitations such as phishing, password theft, and buffer overflow, the attacker can gain access to user accounts and cause damage to existing accounts in various ways. cloud storage faces security challenges in terms of . Encryption keys are stored securely using a hardware security module (hsm), ensuring that keys are never exposed to the cloud service provider. encrypted data is uploaded to azure, and only authorized client side applications can decrypt and access the data using the securely managed keys. Protection of data stored in the cloud is intertwined with the generation, management and lifecycle of cryptographic keys that encrypt this data. we list various options available for protection of data, along with their relative strengths and weaknesses.

Cloud Computing Scalability Data Protection Multi Cloud Data Encryption Data in the cloud is encrypted using algorithms to convert it into unreadable ciphertext, accessible only with decryption keys. the role of data encryption is critical in maintaining the safety and confidentiality of information housed in the cloud. Using vulnerability exploitations such as phishing, password theft, and buffer overflow, the attacker can gain access to user accounts and cause damage to existing accounts in various ways. cloud storage faces security challenges in terms of . Encryption keys are stored securely using a hardware security module (hsm), ensuring that keys are never exposed to the cloud service provider. encrypted data is uploaded to azure, and only authorized client side applications can decrypt and access the data using the securely managed keys. Protection of data stored in the cloud is intertwined with the generation, management and lifecycle of cryptographic keys that encrypt this data. we list various options available for protection of data, along with their relative strengths and weaknesses.
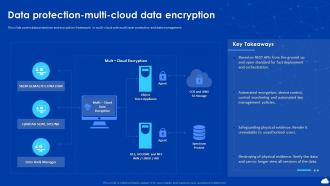
Cloud Automation And Multi Cloud Computing Data Protection Multi Cloud Encryption keys are stored securely using a hardware security module (hsm), ensuring that keys are never exposed to the cloud service provider. encrypted data is uploaded to azure, and only authorized client side applications can decrypt and access the data using the securely managed keys. Protection of data stored in the cloud is intertwined with the generation, management and lifecycle of cryptographic keys that encrypt this data. we list various options available for protection of data, along with their relative strengths and weaknesses.
Comments are closed.