12 Combination Of Secret Key Encryption Public Key Encryption And A

12 Combination Of Secret Key Encryption Public Key Encryption And A Combination of secret key encryption, public key encryption, and a watermarking method person b receives the encrypted and watermarked image, and can then extract the. Which of the following is true about symmetric encryption? a. it uses a private and public key. b. it requires four keys to hold a conversation. c. it uses a secret key to encrypt and decrypt. d. it is also known as public key encryption. it uses a secret key to encrypt and decrypt.

Combination Of Secret Key Encryption Public Key Encryption And A There are many kinds of public key cryptosystems, with different security goals, including digital signature, diffie–hellman key exchange, public key key encapsulation, and public key encryption. Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or verify signatures, and a private key, which is kept secret and used to decrypt messages or sign documents. We construct a public key encryption scheme Πhy = (genhy , enchy , dechy) as follows: theorem 11.12: if Π is a cpa secure kem and Π’ is a private key encryption scheme that has indistinguishable encryptions in the presence of an eaves dropper, then Πhy is a cpa secure public key encryption scheme. Diffie–hellman key exchange allows two parties to jointly establish a shared secret key over an insecure communication channel the established key can then be used to encrypt subsequent communication using a symmetric key cipher “new directions in cryptography” by whitfield diffie and martin hellman, 1976 based on the discrete logarithm.

Public Key Private Key Encryption Java 12 Ships We construct a public key encryption scheme Πhy = (genhy , enchy , dechy) as follows: theorem 11.12: if Π is a cpa secure kem and Π’ is a private key encryption scheme that has indistinguishable encryptions in the presence of an eaves dropper, then Πhy is a cpa secure public key encryption scheme. Diffie–hellman key exchange allows two parties to jointly establish a shared secret key over an insecure communication channel the established key can then be used to encrypt subsequent communication using a symmetric key cipher “new directions in cryptography” by whitfield diffie and martin hellman, 1976 based on the discrete logarithm. Modern secret key cryptography messages encrypted and decrypted with a shared secret key usually the same key for both operations ("symmetric"). Asymmetric (public key) encryption: alice has a secret decryption key dk that is shared with nobody, and an associated public encryption key ek that is known to everybody. anyone (bob, charlie, . . .) can use alice’s encryption key ek to send her an encrypted message which only she can decrypt. Gen(1k) outputs a pair of keys (p k; sk); the public and private keys respectively. enc(p k; m) encrypts a message m under public key p k. dec(sk; c) decrypts a ciphertext c under secret key sk. There are two basic types of cryptography: secret key systems (also called symmetric systems) and public key systems (also called asymmetric systems). table 19.1 compares some of the distinct features of secret and public key systems. both types of systems offer advantages and disadvantages.
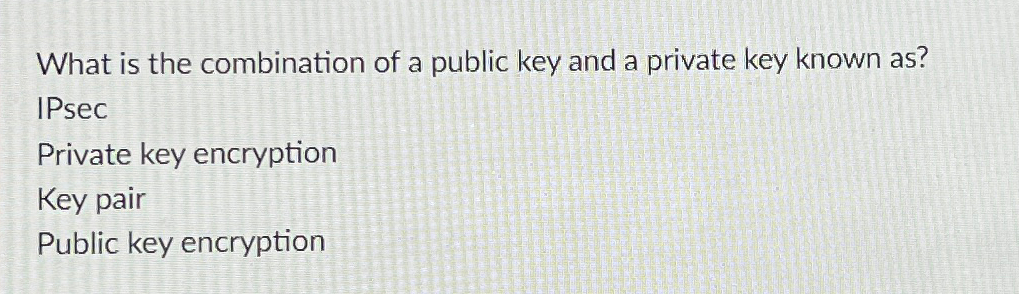
Solved What Is The Combination Of A Public Key And A Private Chegg Modern secret key cryptography messages encrypted and decrypted with a shared secret key usually the same key for both operations ("symmetric"). Asymmetric (public key) encryption: alice has a secret decryption key dk that is shared with nobody, and an associated public encryption key ek that is known to everybody. anyone (bob, charlie, . . .) can use alice’s encryption key ek to send her an encrypted message which only she can decrypt. Gen(1k) outputs a pair of keys (p k; sk); the public and private keys respectively. enc(p k; m) encrypts a message m under public key p k. dec(sk; c) decrypts a ciphertext c under secret key sk. There are two basic types of cryptography: secret key systems (also called symmetric systems) and public key systems (also called asymmetric systems). table 19.1 compares some of the distinct features of secret and public key systems. both types of systems offer advantages and disadvantages.

Public Key And Private Key Encryption Difference Asta Coin Gen(1k) outputs a pair of keys (p k; sk); the public and private keys respectively. enc(p k; m) encrypts a message m under public key p k. dec(sk; c) decrypts a ciphertext c under secret key sk. There are two basic types of cryptography: secret key systems (also called symmetric systems) and public key systems (also called asymmetric systems). table 19.1 compares some of the distinct features of secret and public key systems. both types of systems offer advantages and disadvantages.
Comments are closed.